Why Does MITRE ATT&CK Matter?
Recently, Ardalyst had the opportunity to attend MITRE’s inaugural cyber security conference for industry, government, and academia to share best practices for MITRE ATT&CKcon. The event was held October 23-24 at MITRE’s McLean, VA headquarters with hundreds gathered to help shape the MITRE ATT&CK Enterprise Framework.
As described by MITRE in MITRE ATT&CK™: Design and Philosophy, “MITRE’s Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK) is a curated knowledge base and model for cyber adversary behavior, reflecting the various phases of an adversary’s attack lifecycle and the platforms they are known to target. ATT&CK originated out of a project to enumerate and categorize post-compromise adversary tactics, techniques and procedures (TTPs) against Microsoft Windows™ systems to improve detection of malicious activity. It has since grown to include Linux™ and MacOS™, and has expanded to cover pre-compromise tactics and techniques, and technology-focused domains like mobile devices.”
To be fair, Ardalyst is an early adopter of ATT&CK in its application of systematically categorizing adversary behavior as part of an overarching design in tailoring cyber defense strategies to counter specific adversary threats. Over the last five years, we have seen the framework mature from its humble beginning of improving host-based detection through threat emulation, and what Gary Gagnon, MITRE Senior Vice President and Chief Information Security Officer, acknowledged at the conference as threat deception operations. We believe what we saw at the MITRE ATT&CK Conference will be an inflection point in the cyber security industry ecosystem.
There is a long way to go until cyber threat management, threat informed cyber defense, and commercial cyber threat intelligence systems become mainstream. However, we did witness was the concrete place from where they accelerate to become a foundational requirement for a (cyber) security operations center to be considered legitimate.
So, Why does ATT&CK Matter?
Similar to what MITRE did for cyber vulnerability management with the release of the Common Vulnerabilities and Exposures (CVE) system in 1999 to share and organize known cyber vulnerabilities, ATT&CK provides the means to share and organize known cyber threat tactics, techniques, and procedures (TTP). It took a decade for vulnerability management to become mainstream in basic information technology operations and tools. CVE became the basis, however, of information security’s journey from regulation, policy, and compliance through computer security scanners and management tools and into computer network defense (CND) intrusion detection systems (IDS).
IDS have matured over the years looking for known bad files, known bad Internet address or domain names to something more nuanced. In 2013, David Bianco described this as the Pyramid of Pain in response to the Mandiant APT 1 report. He used the pyramid to describe how hard or easy it was for adversaries to change their methods and avoid detection via these devices. Bianco’s point is that no one was really using indicators of compromise (IOCs) correctly from these published intelligence reports – IOCs were all about bad hashes, IP addresses, and domain names.
TTPs are incredibly hard to change every time you hack a system and there are frankly only so many ways to do it.
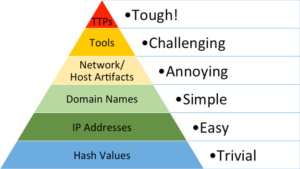
Although there are so many ways to hack a system, they are not all the same. The point of ATT&CK was to start systematically categorizing and describing them to develop the same language to differentiate between those TTPs that were well known and quickly recognize and share the truly novel.
The 2018 MITRE ATT&CKcon is likely to be the inflection point for threat-based cyber defense. Over the next several years, we expect to see ATT&CK used as the basis of comparing endpoint detect and response (EDR) tools. We believe network detection and response tools will soon follow, until threat TTP based detection and response is inherent to most digital productivity platforms.





