Since 2014, the Federal Information Security Modernization Act (FISMA) has required federal agencies to implement a program that provides security for all of the information and systems that support their operations, including those provided for and managed by third parties. As such, DoD contractors are required to follow the National Institute of Standards and Technology (NIST) Risk Management Framework (RMF) Special Publication (SP) 800-37.
The Risk Management Framework defines a process for integrating security, privacy, and cyber supply chain risk management activities into the system development life cycle. The risk-based approach to control selection and specification considers effectiveness, efficiency, and constraints imposed by applicable laws, directives, Executive Orders, policies, standards, or regulations. The RMF approach can be applied to new and legacy systems, any system or technology (e.g., IoT, control systems), and within any size or sector of the organization.
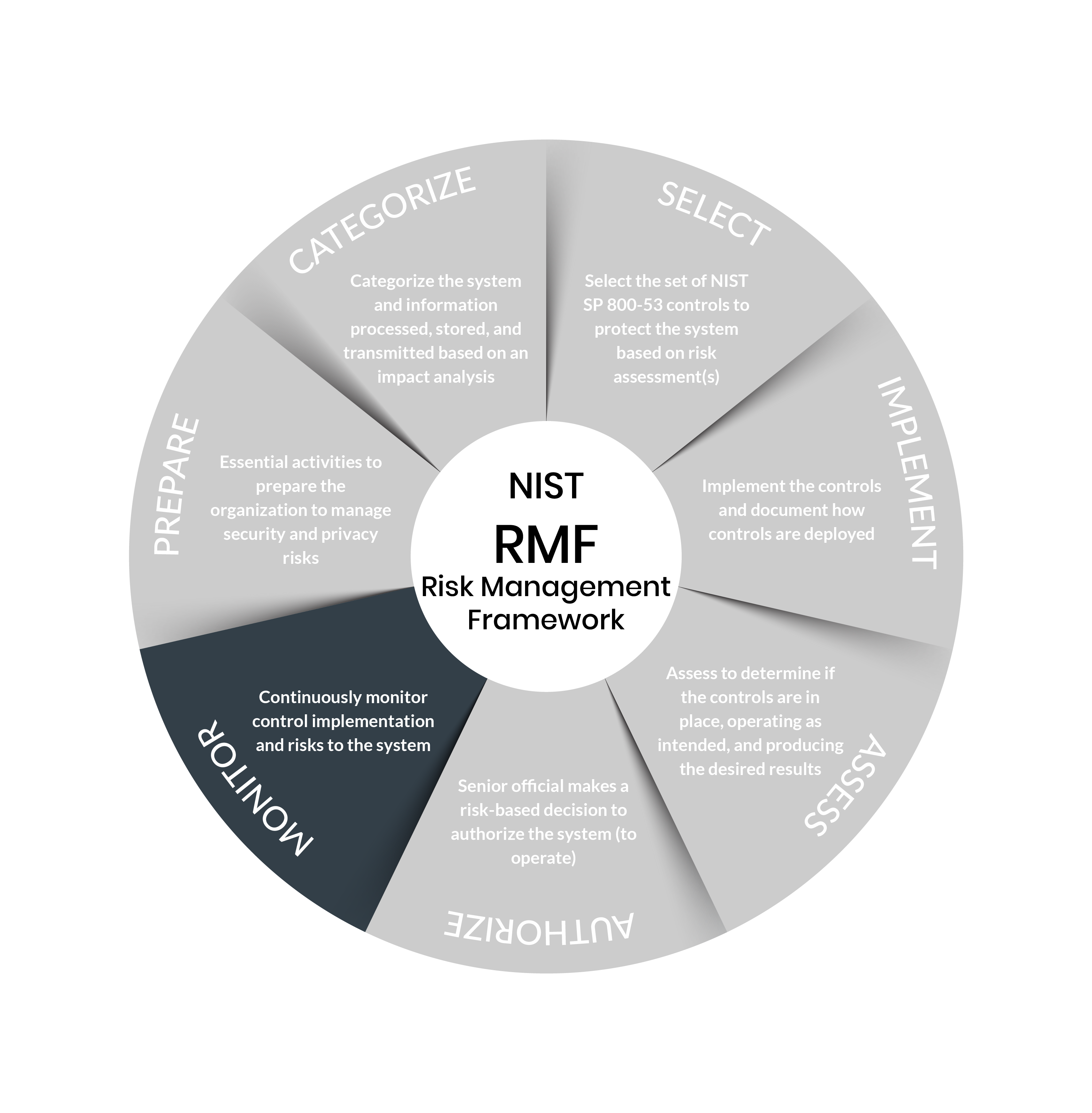
Risk Management Framework Steps
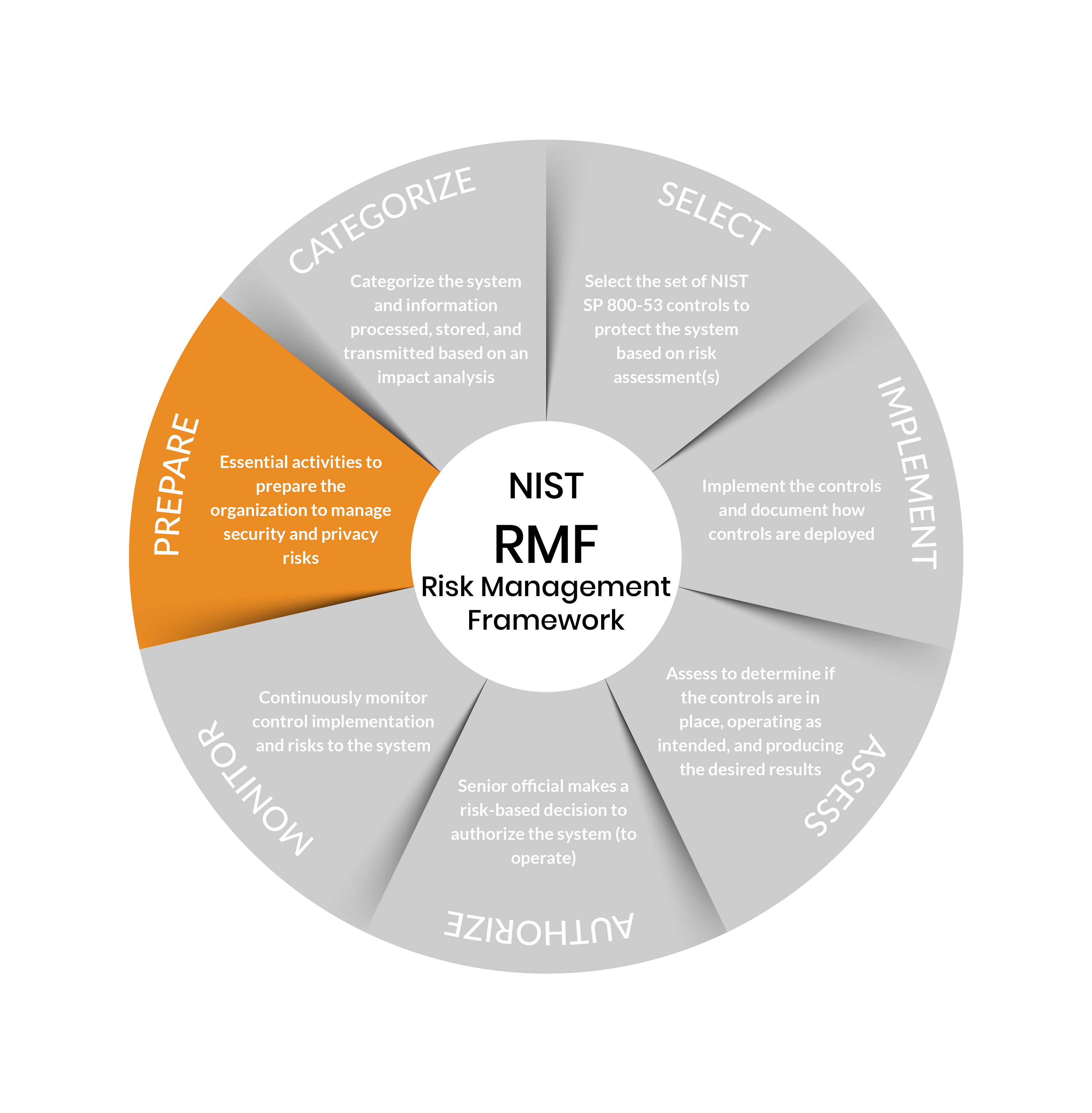
Step 1: Prepare
Purpose: Carry out essential activities to help prepare all levels of the organization to manage its security and privacy risks using the RMF.
Outcomes:
- Key risk management roles identified
- Organization risk management strategy established, risk tolerance determined
- Organization-wide risk assessment
- Organization-wide strategy for continuous monitoring developed and implemented
- Common controls identified
Source: https://csrc.nist.gov/Projects/risk-management/about-rmf/prepare-step
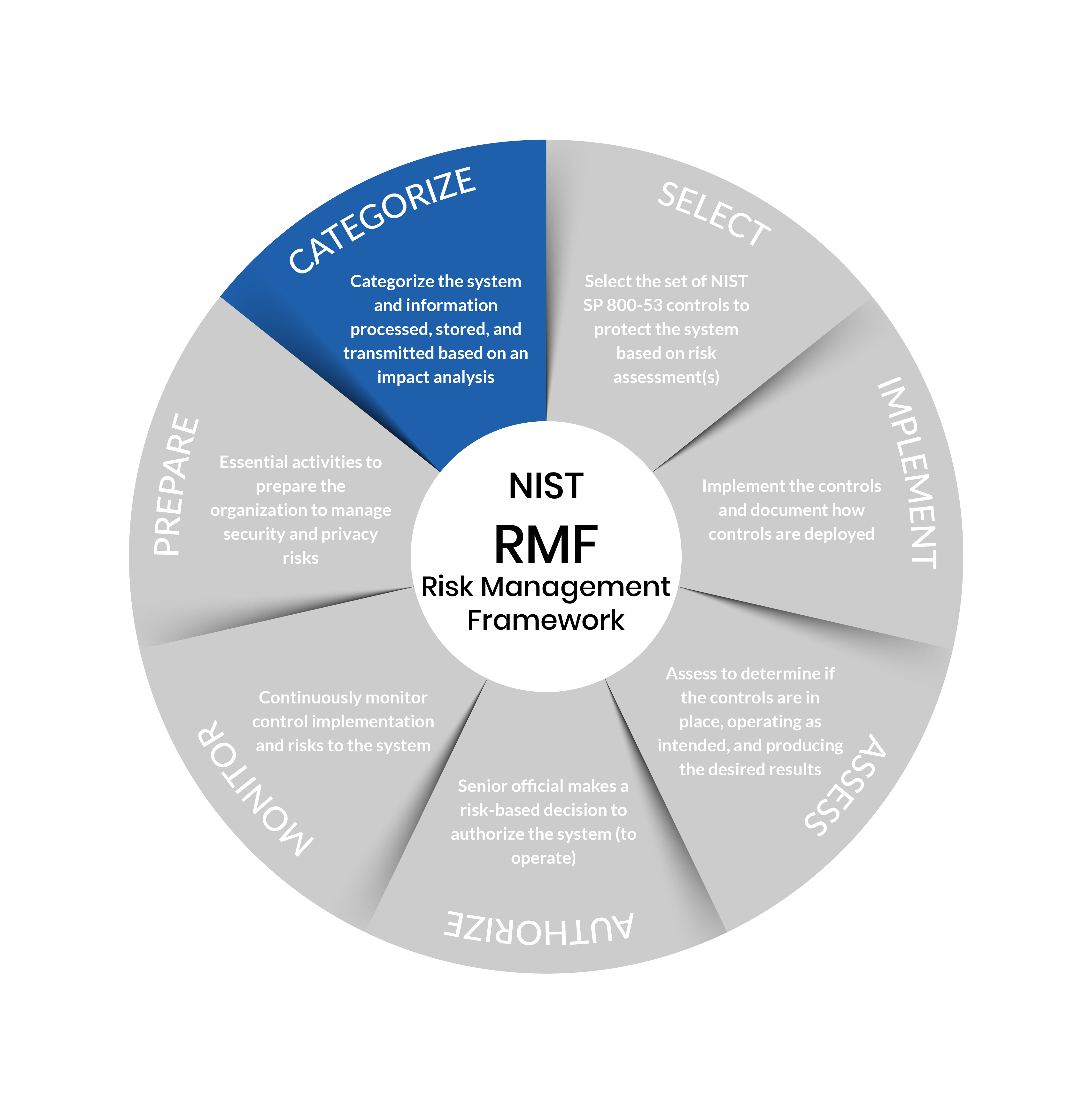
Step 2: Categorize
Purpose: Inform organizational risk management processes and tasks by determining the adverse impact with respect to the loss of confidentiality, integrity, and availability of systems and the information processed, stored, and transmitted by those systems.
Outcomes:
- System characteristics documented
- Security categorization of the system and information completed
- Categorization decision reviewed/approved by authorizing official
Source: https://csrc.nist.gov/Projects/risk-management/about-rmf/categorize-step
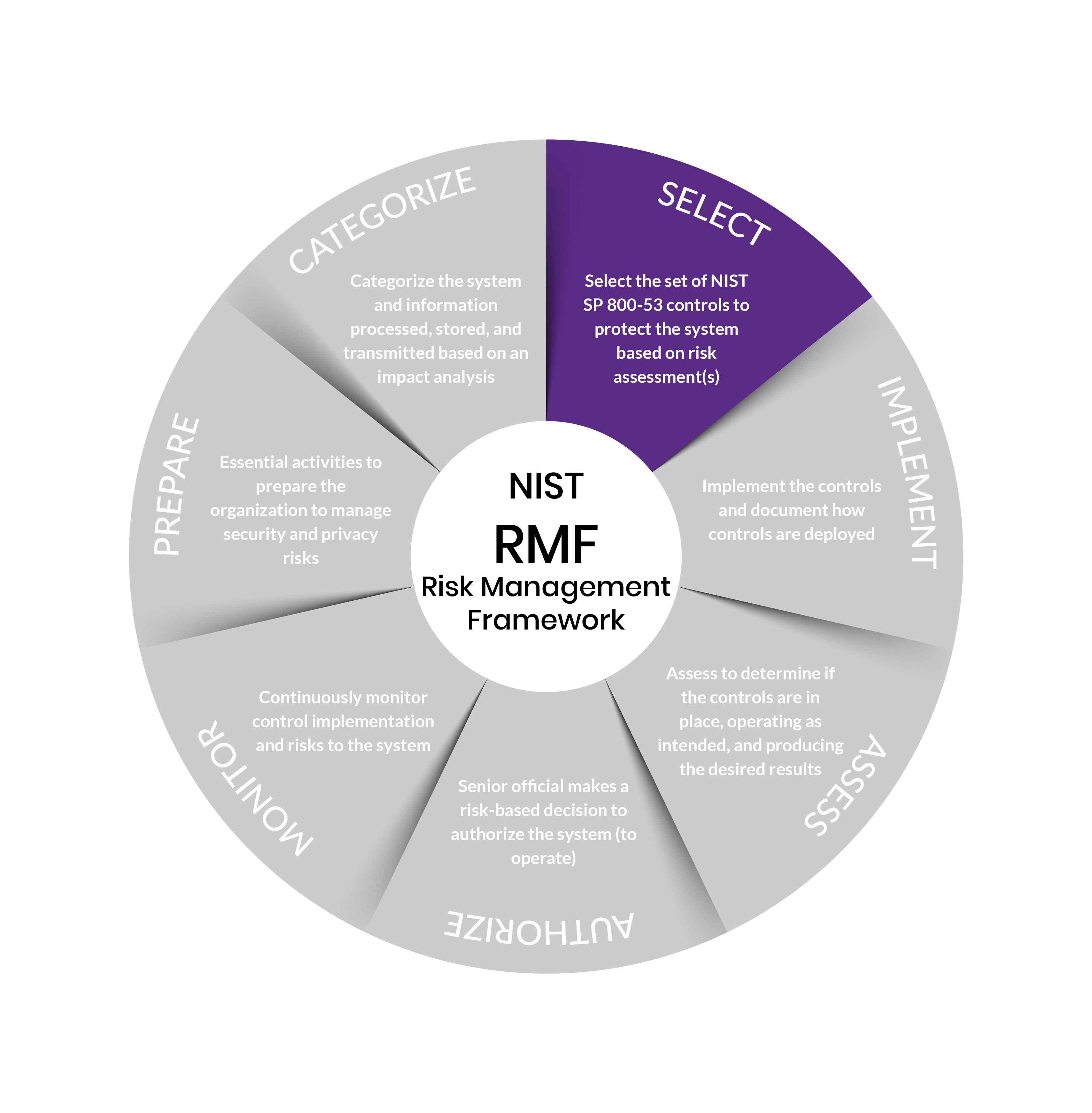
Step 3: Select
Purpose: Select, tailor, and document the controls necessary to protect the system and organization commensurate with risk.
Outcomes:
- Control baselines selected and tailored
- Controls designated as system-specific, hybrid, or common
- Controls allocated to specific system components
- System-level continuous monitoring strategy developed
- Security and privacy plans that reflect the control selection, designation, and allocation are reviewed and approved
Source: https://csrc.nist.gov/Projects/risk-management/about-rmf/select-step
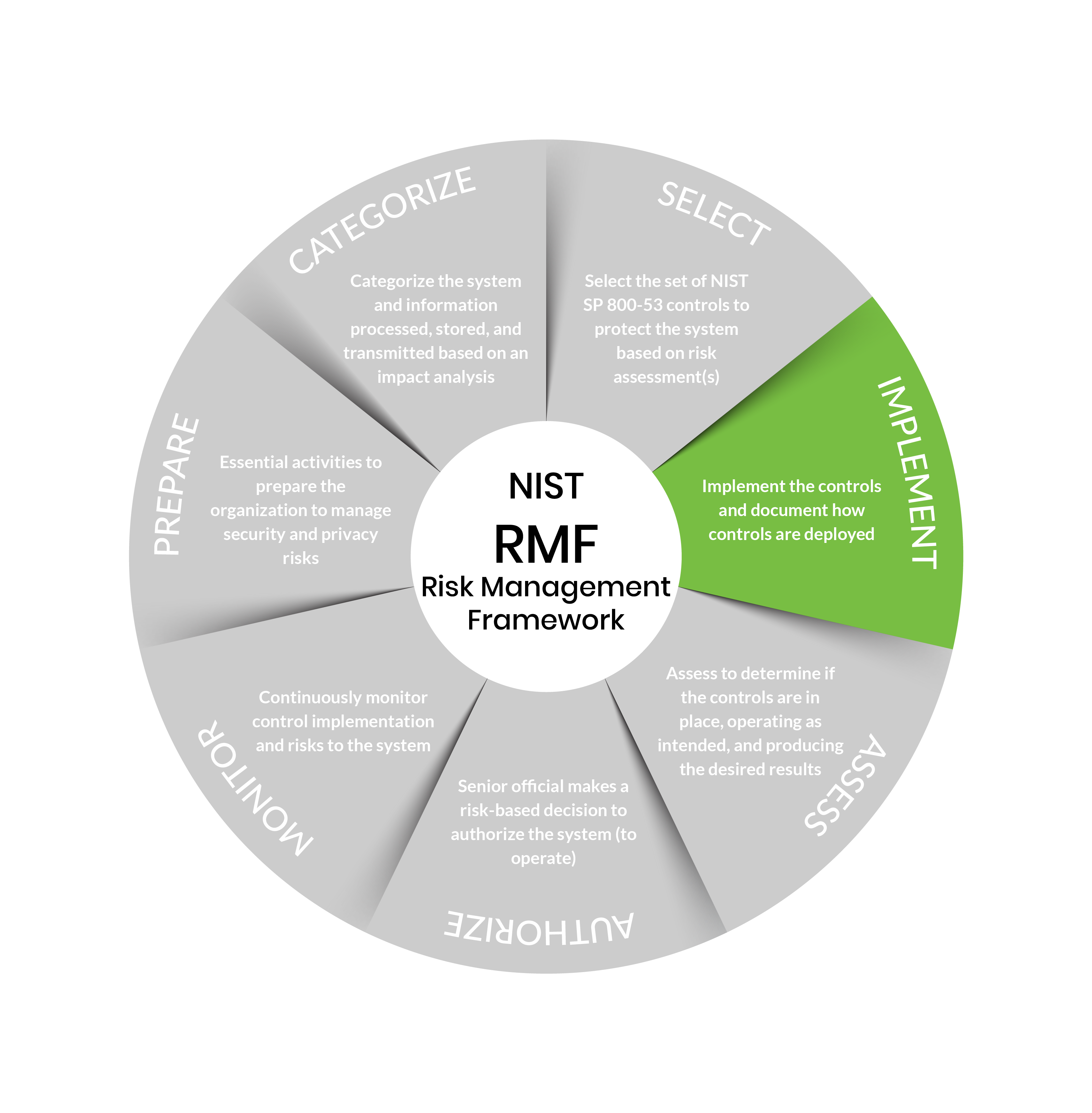
Step 4: Implement
Purpose: Implement the controls in the security and privacy plans for the system and organization.
Outcomes:
- Controls specified in security and privacy plans implemented
- Security and privacy plans updated to reflect controls as implemented
Source: https://csrc.nist.gov/Projects/risk-management/about-rmf/implement-step
Step 5: Assess
Purpose: Determine if the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security and privacy requirements for the system and the organization.
Outcomes:
- Assessor/assessment team selected
- Security and privacy assessment plans developed
- Assessment plans are reviewed and approved
- Control assessments conducted in accordance with assessment plans
- Security and privacy assessment reports developed
- Remediation actions to address deficiencies in controls are taken
- Security and privacy plans are updated to reflect control implementation changes based on assessments and remediation actions
- Plan of action and milestones developed
Source: https://csrc.nist.gov/Projects/risk-management/about-rmf/assess-step
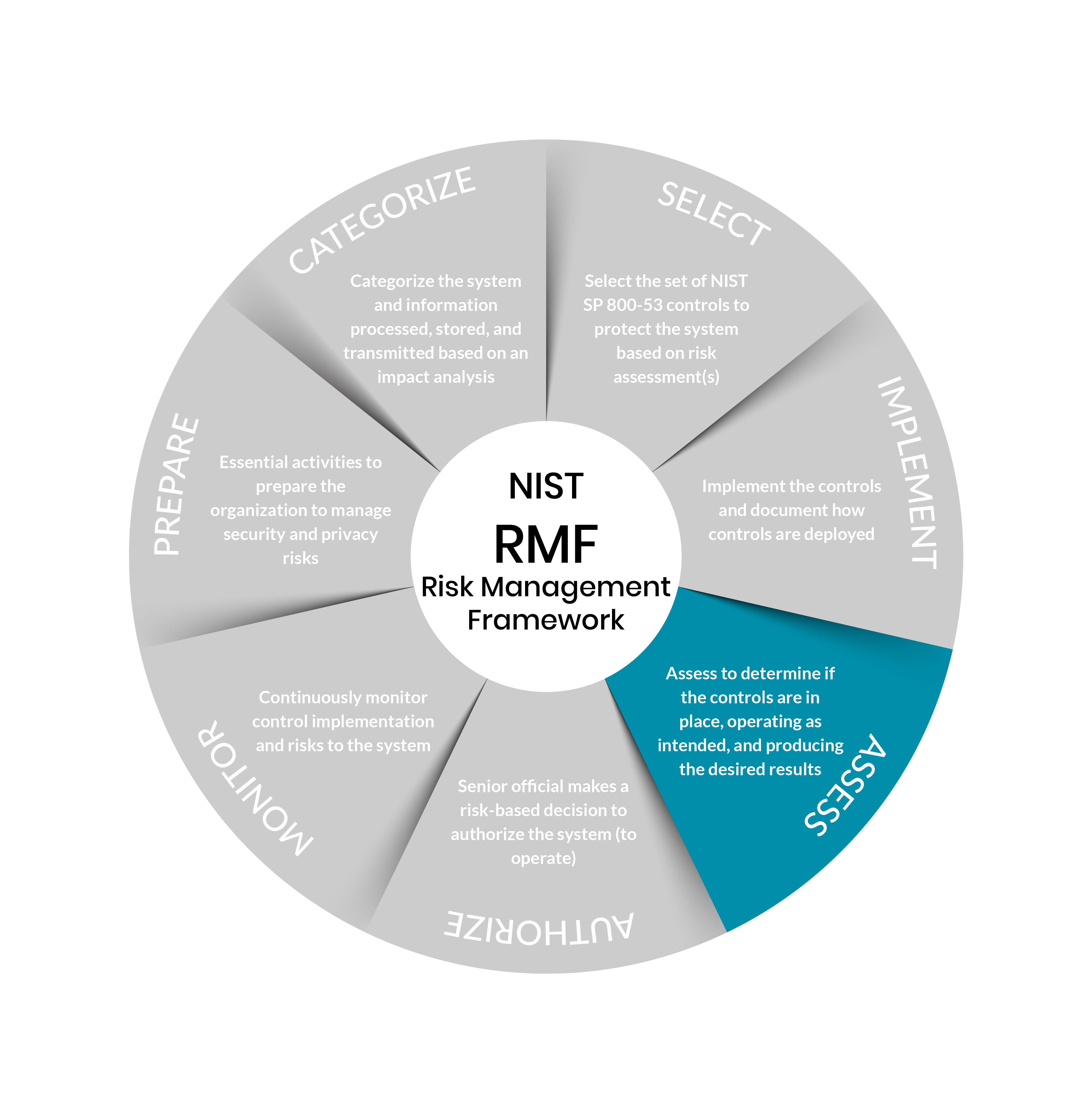
Step 6: Authorize
Purpose: Provide accountability by requiring a senior official to determine if the security and privacy risk based on the operation of a system or the use of common controls, is acceptable.
Outcomes:
- Authorization package (executive summary, system security and privacy plan, assessment report(s), plan of action and milestones)
- Risk determination rendered
- Risk responses provided
- Authorization for the system or common controls is approved or denied
Source: https://csrc.nist.gov/Projects/risk-management/about-rmf/authorize-step
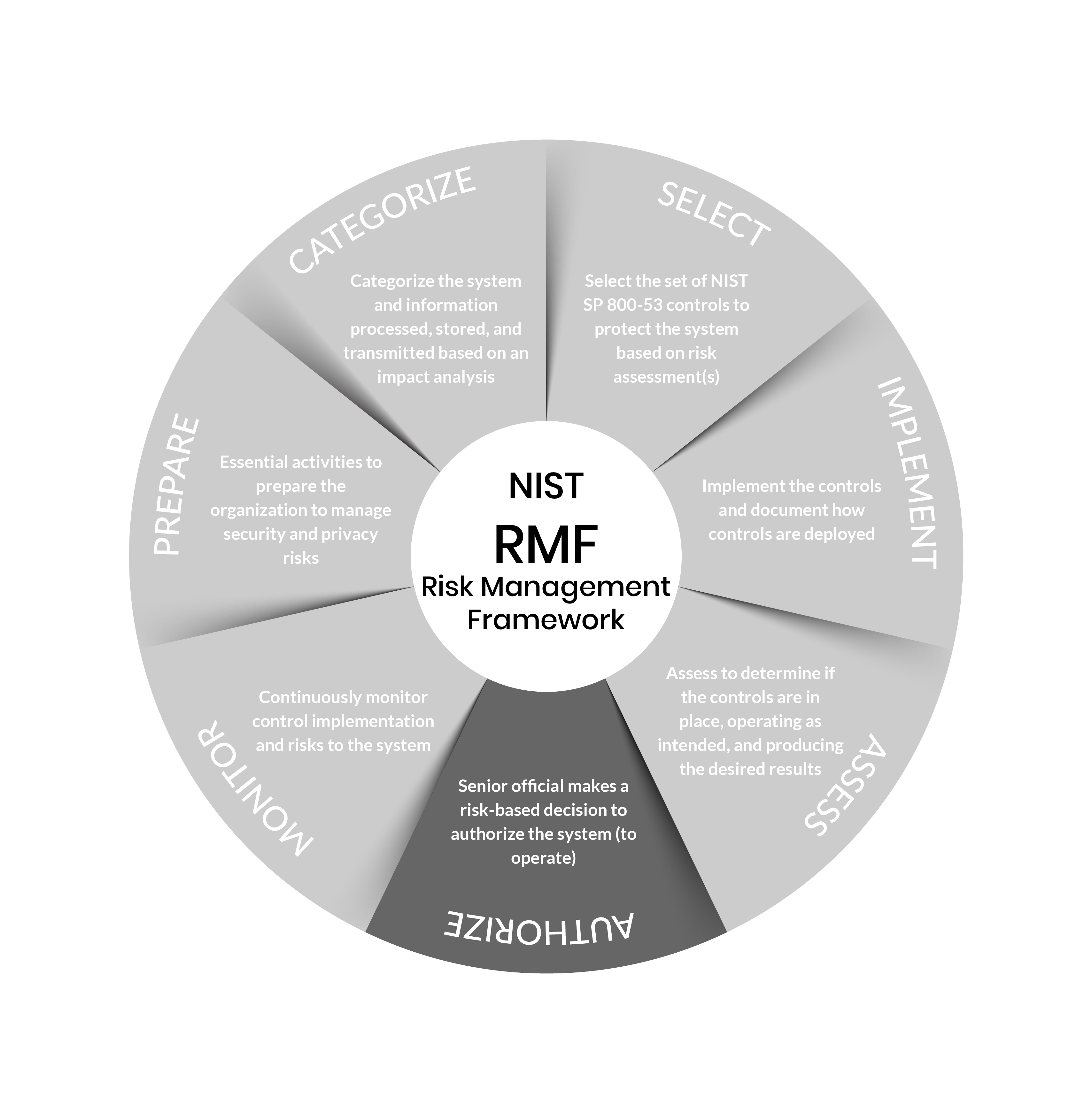
Step 7: Monitor
Purpose: Maintain ongoing situational awareness about the security and privacy posture of the system and organization to support risk management decisions.
Outcomes:
- System and environment of operation monitored in accordance with continuous monitoring strategy
- Ongoing assessments of control effectiveness conducted in accordance with continuous monitoring strategy
- Output of continuous monitoring activities analyzed and responded to
- Process in place to report security and privacy posture to management
- Ongoing authorizations conducted using results of continuous monitoring activities
Source: https://csrc.nist.gov/Projects/risk-management/about-rmf/monitor-step
The Assessment & Authorization (A&A) Process
Obtaining Authority to Operate (ATO)
The A&A process, sometimes referred to as the Certification & Accreditation (C&A) process is a comprehensive evaluation of your organization’s policies, security controls, and vulnerabilities. The A&A evaluates how well you have implemented the steps of the RMF and is confirmed via an Authorization to Operate (ATO).
Risk Management Framework Services & Support
Building a compliant cybersecurity program, getting all the right documentation together, and going through the A&A process to receive your ATO can be challenging and requires both compliance expertise and quite a bit of cyber engineering. Ardalyst’s team of cyber and compliance experts bring over 100+ years of combined experience to serving DoD contractors looking to implement NIST’s Risk Management Framework (RMF). Whether helping you to develop or revamp a compliant cybersecurity program to meet the RMF controls of NIST 800-53, preparing your business for the Defense Counterintelligence Agency’s (DCSA) accreditation process, or building approaches to special access programs, our experts:
- develop the right policies and procedures for your program;
- implement security controls, architectures, and validation; and
- author, review, or contribute to your System Security Plan, Security Control Traceability Matrix, Security Assessment Review; Risk Assessment Review; and Plan of Actions & Milestones.
Our experts will be with you every step of the way of your ATO process, from package authoring to submission. Beyond, our consulting and managed services teams can help implement your program and supplement your teams to RMF continuous monitoring activities.

Consulting & Security Documentation
Your dedicated Ardalyst Advisor will review existing documentation and work with your key stakeholders to update your cybersecurity policies and procedures, and other required security documentation for your business. This includes:
- System Security Plan (SSP)
- Security Assessment Plan
- Security Assessment Report
- Risk Assessment Report
- Privacy Impact Assessment
- RMF Validation Plan and Procedures
- System Security Categorization Federal Information Processing Standards (FIPS) 199
- Validation Security Test & Evaluation (ST&E) Report / ST&E Plan and Results
- Plan of Action & Milestones (POAM)
- Contingency Plan

Gap Identification & Remediation
Our RMF experts will review your current cybersecurity program and practices. This assessment will determine that your controls are properly implemented and, if needed, lay the foundation for your RMF A&A strategy, including developing your A&A schedule outlining all major project phases and recommended next steps.
- Determine any missing steps and RMF requirements
- Policy research and documentation
- NIST 800-53 security controls implementation & validation
- DISA Secure Technical Implementation Guide (STIG) software images of all systems

Assessment & Authorization (A&A) Support
Ardalyst A&A support services work hand-in-hand with your cybersecurity system administrator(s) to collaborate on final documentation review and submit your RMF package to obtain your ATO. These services include:
- RMF package generation & review
- Authorizing Official (AO) Briefing
- Authorization Package Submission / eMASS upload and management
- Collaborating with AO to mitigate and remediate outstanding vulnerabilities