Build for Cyber Resiliency
Limit dependencies on vulnerable technologies and processes.
Stay Ahead of Threats
Regularly adjust your security based on the threats you face.
Develop Greater Assurance
Protect the system with out-of-band feedback to demonstrate and validate your system security.
Evolve with the Adversary
Leverage the latest understanding of your adversaries in your defenses.
Zero Trust Architecture is a data-centric cybersecurity model for access management employed without trusting the operating environment. In an ideal world, a true Zero Trust cybersecurity system could be the only cybersecurity system you need, as you are collecting all data and using it to make every access decision. The unfortunate truth is that, currently, that kind of data collection, curation, and analysis to drive accurate decisions on every interaction can be messy, inefficient, and exploited. This doesn’t mean that Zero Trust is without merit, only that it should not be your sole cybersecurity strategy. And with Ardalyst, it isn’t.
With no way to prove the security of a system, we designed an architecture that doesn't require it...
Implement a stronger defense against any attacker and any threat. While Zero-Trust provides a strong foundation, adversaries are adapting their techniques and tactics. How do you prove your ZTA is secure when no proof of adversaries isn’t proof of no adversaries? With no way to prove the security of a system, we designed an architecture that doesn’t need it. Get the resilience you need in the face of advanced threats with the All-Threat approach.
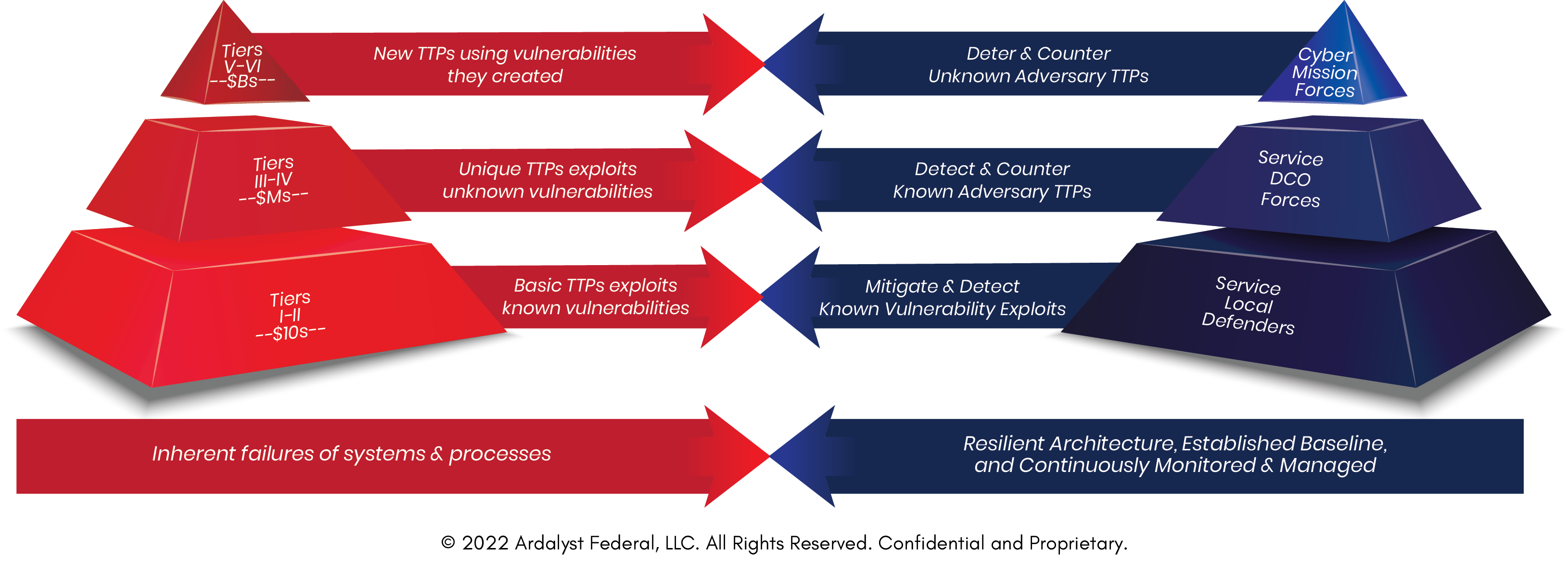
Ardalyst’s All-Threat™ Zero-Trust Architecture is built on an intelligence-led, zero-trust-based, balanced-systems approach to protecting your organization against all tiers of cyber threats. By integrating Microsoft’s ZTA, Endpoint Security, and Mandiant’s Threat Intelligence combined with Ardalyst capabilities, we can help your business create a Zero Trust Architecture that is resilient against different (i.e., all) tiers of threats.

Leverage the Cybersecurity Capabilities Baked Right Into Microsoft 365
Easily manage low to mid-tier threats and build your core zero trust architecture.
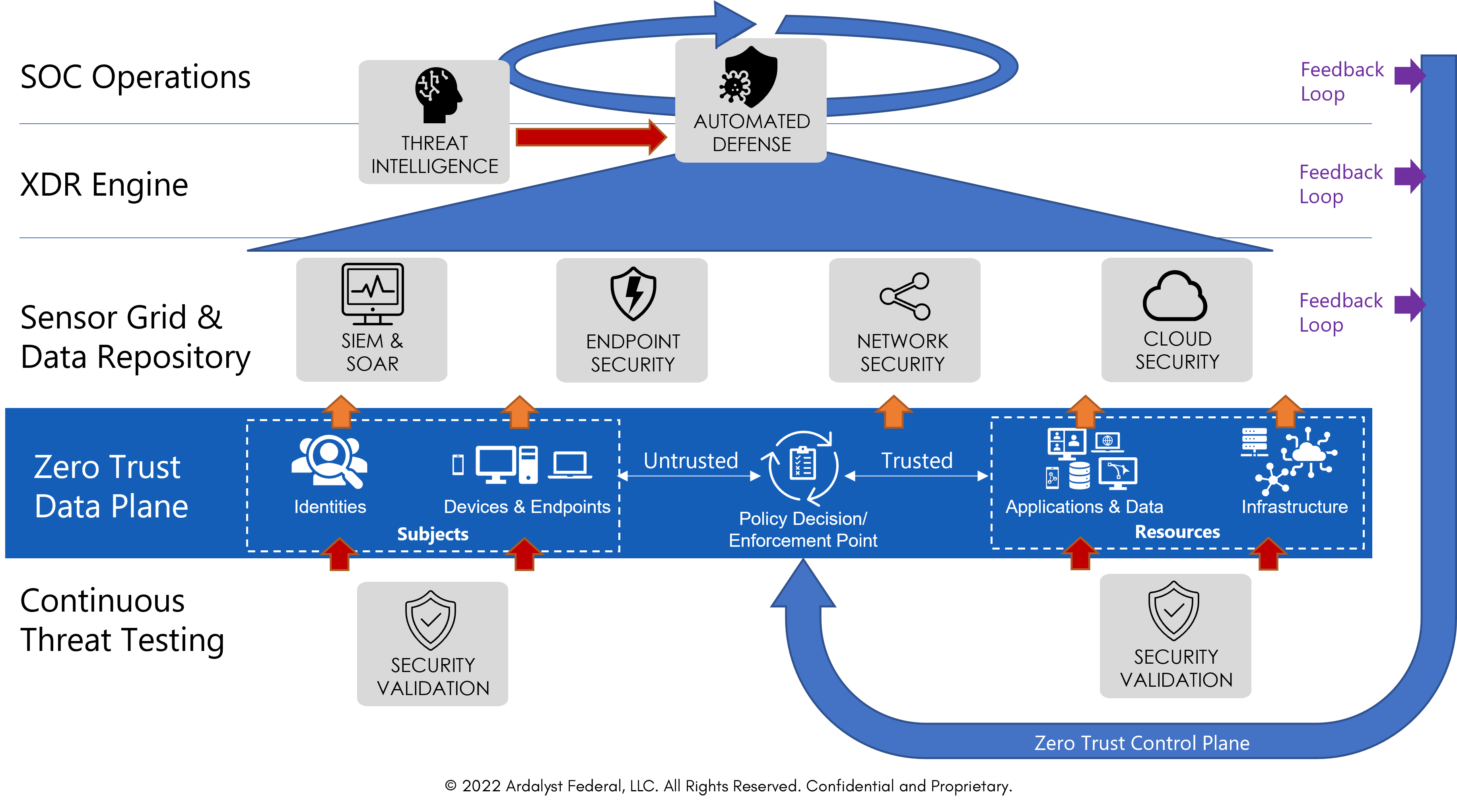
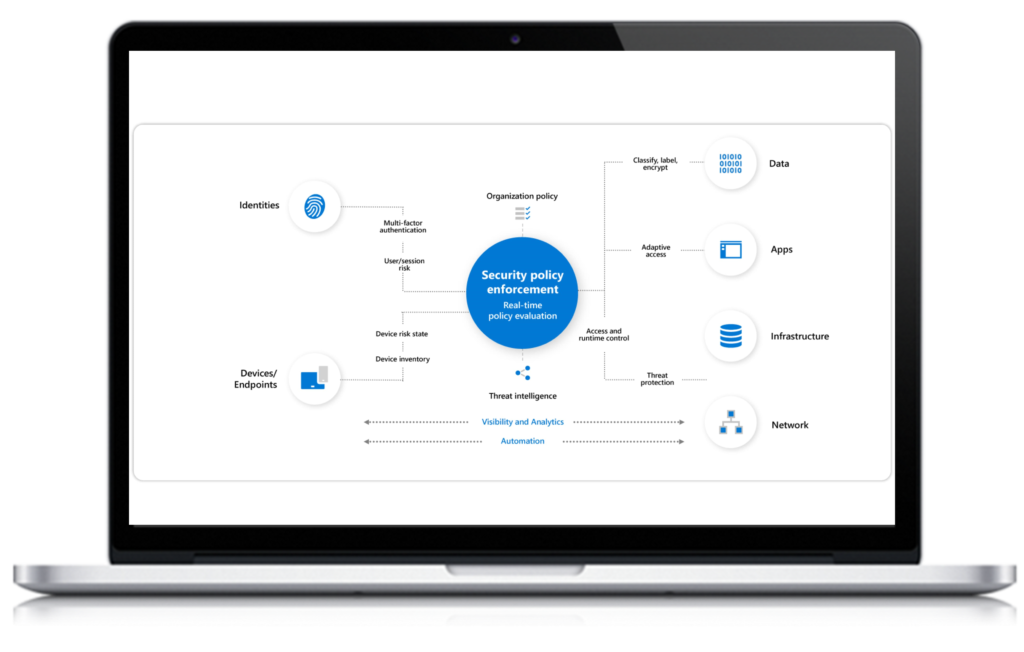
Policy Enforcement Point
Azure Active Directory (AD) with Risk-based Conditional Access is the key mechanism in the Microsoft Zero Trust Architecture (ZTA) for enforcing policies on transactions.
Identity
Azure AD Identity Protection automates the detection and remediation of identity-based risks.
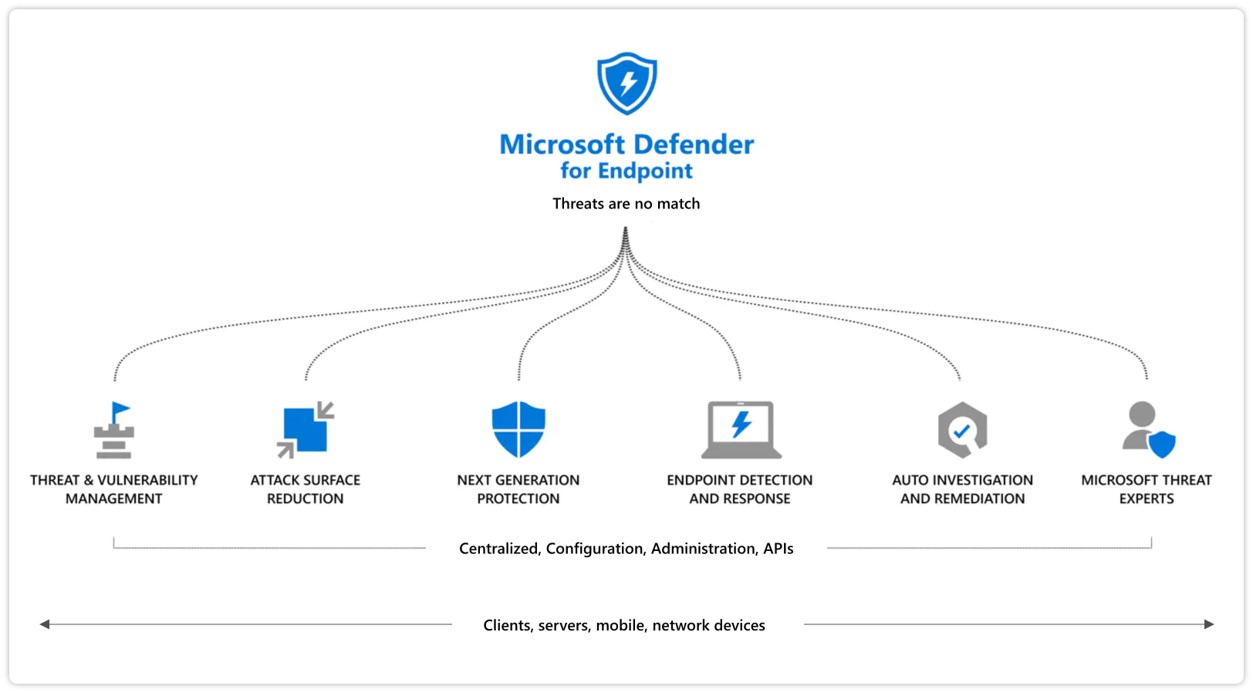
Endpoints
Microsoft Endpoint Manager (MEM) ensures devices meet security and compliance policies. Microsoft Defender for Endpoint (MDE) integrates a full suite of endpoint security into your ZTA.
Infrastructure
Azure Security Center monitors infrastructure security posture and compliance. Azure Defender detects and blocks malware and threats across servers, data, cloud-native services, and IoT.
Applications & Data
Microsoft Cloud App Security (MCAS) provides end-to-end protection for cloud apps. Azure Purview provides unified governance for on-premises, multi-cloud, and Software-as-a-Service data.
Building Advance Threat Intelligence & Security Validation Into Your System
A strong cyber defense against mid to high-tier threats.
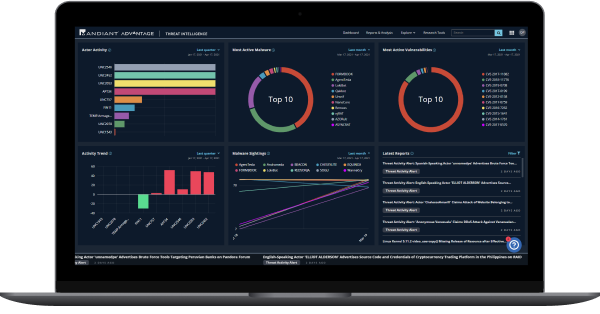
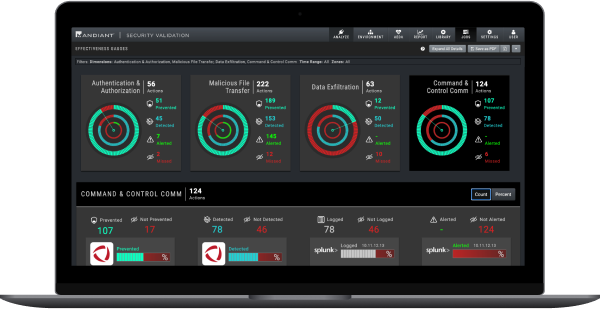
Threat-Based Continuous Monitoring
Mandiant Security Validation (MSV) continuously tests the effectiveness of implemented security controls using automated threat emulation.
Sensor Grid & Data Responsitory
Data collection for Extended Detection and Response (XDR) is integrated together to detect advanced adversarial activities when the inline protection fails.
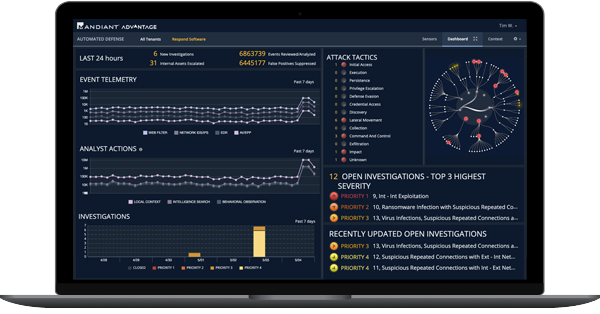
Automated Threat Management
Mandiant Automated Defense combines pre-built data science models with threat intelligence, the XDR, and core Zero Trust components to enrich escalation and prioritization.
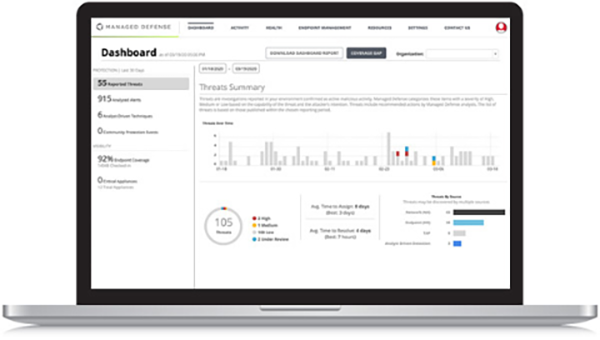
Cyber Defense Augmentation
Mandiant Managed Defense and Expertise-on-Demand provide security operations access to scalable cyber defense expertise without building a cyber defense operations center.
The All Threat™ Difference
A Multi-Tiered Strategy for Multi-Tiered Threats
Zero Trust Technology
Achieving Cyber Resiliency in Zero Trust with Microsoft & iBoss
Cyber Defense Technology
Achieving Cyber Resiliency in Zero Trust with Microsoft
All Threat Intelligence Integration
Achieving Cyber Resiliency in Zero Trust with Mandiant