Security Operations Centers (SOCs) of the Future
Medici Moons
Next-Generation Protection for Next-Level Threats
The cybersecurity threat landscape is ever changing and we need solutions that can combat the cunning and opportunistic adversaries that are eager to exploit the shortcomings in our defense systems. With the recent cyber incident that shut down the Colonial Pipeline for several days and the subsequent Executive Order, there is now a greater demand for attention to cybersecurity measures that can stand up to our adversaries and evolve to meet the challenge of changing threat vectors. Today's Security Operations Centers (SOCs) also need to be able to protect us in the world we live in today, meaning hybrid IT infrastructures, complex and growing multi-tenant/multi-site enterprises and networks, and cloud-based environments.
SOCs of the Future
Introducing Medici Moons
Medici Moons is a next-generation SOC design that addresses the need for greater threat awareness, validation, rapid response, and remediation by improving the collection, curation, and analysis of information to arm security teams with actionable intelligence for better preparation for today -and tomorrow’s- cybersecurity risk. With its multiple SOCs, advanced sensors, and numerous potential technical innovations, the Medici Moons design will show that new technologies and updated tactics, techniques, and procedures will change the way we think about the future of cyber defense.
Named after the Galilean moons that surround Jupiter, Medici Moons reflects the innovative spirit that the great astronomer showed when he developed a high-powered telescope to view these previously unknown objects. But, instead of looking into actual space, we’re able to see things that are happening in cyberspace that could adversely impact a data center.
Medici Moons
The Concept
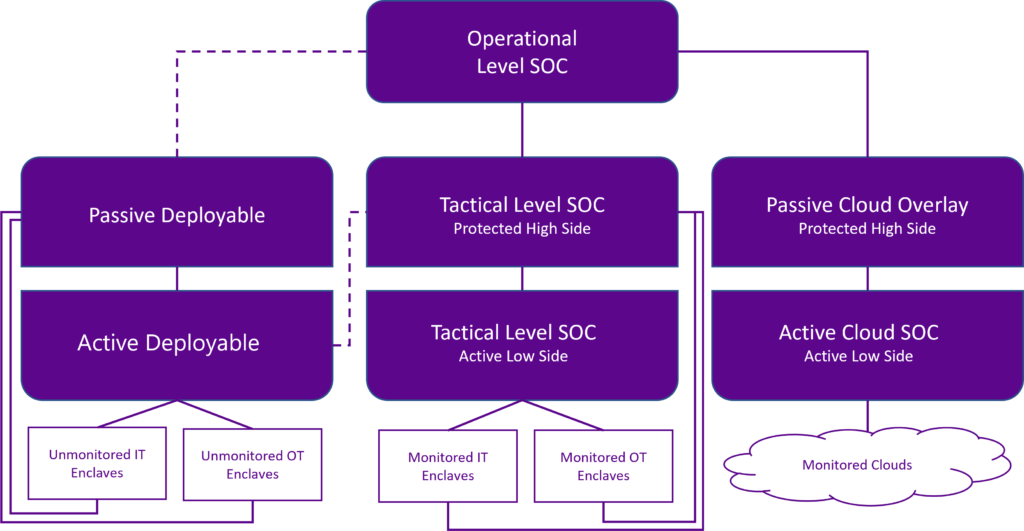
Medici Moons includes a distributed, operational-level cybersecurity operations center (CSOC) which manages and receives data from the tactical-level CSOC. The tactical CSOC is made up of an active, low-side enclave that provides initial collection and automated response, as well as a secondary passive, high-side enclave that provides out-of-band collection activities.
The design integrates the best of various levels of capabilities across physical and software-defined architectures to allow for a rapid threat response while automatically mitigating threats across physical, virtualized, and cloud-based infrastructures. It also provides actionable intelligence that lets teams anticipate, withstand, recover, and evolve from attacks.
Cyber Defense Technology
Integrated Capabilities




