Ardalyst Cybersecurity Program Roadmap to Cyber Resilience
Ardalyst will work together with you to assess the current state of your cybersecurity program and develop a plan to work toward full maturity at a pace and cost that meets your goals.
Step 1
Determine the Maturity of your Cyber Resilience Program
A comprehensive and mature cybersecurity program requires a wide range of capabilities. To focus your cybersecurity strategy, plan to achieve your compliance and maturity goals through the following lenses:
Govern
Ensure your organization is doing the right things to develop and maintain up-to-date policies and procedures that help you maintain compliance with changing regulations.
Harden
Implement capabilities that reduce your vulnerabilities and make it difficult for the adversary to access and compromise your environment.
Defend
Leverage tools that increase your knowledge of threats and help your organization
rapidly identify and respond to them.
Step 2
Establish Clear Program Goals
Consider your goals and scope. What level of cyber maturity makes sense for your organization? What certifications do you want? What certifications do you need? We can help determine what and where your needs are based on your unique organization and what we can provide on our menu of options.
Step 3
Determine Scope & Timeline
For some clients, the needed investment in people, processes and technology can be daunting. It’s not necessary to go “all in” right away. Our practical, no-pressure approach helps you identify what capabilities are best purchased at the best time with the right investment.
Crawl … walk … run. It’s up to you. Your cyber portfolio is completely customizable based on immediate and future priorities. We work on your timeline, within your budget and meet your needs.
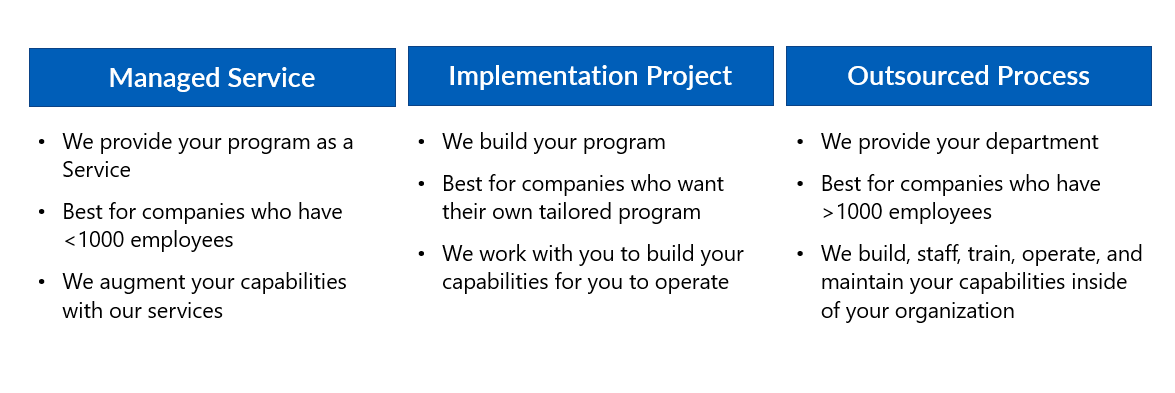
Step 4
Select a Vendor Strategy
When choosing a provider, companies generally have three options for outsourcing their cybersecurity maturity along the spectrum of program vs point solutions.
-
Configure your systems – Hire a provider with in-depth knowledge of cyber defense and regulatory requirements to tailor capabilities to your specific needs, set up and configure the architecture, then turn it over to your in-house IT team to implement and maintain.
-
Implement your cybersecurity program – Hire a provider with in-depth knowledge of cyber defense and regulations to set up, configure, and implement some of the capabilities before turning it over to your in-house team to maintain.
-
Sustain and manage your cybersecurity program – Hire a provider to supply ongoing services, essentially outsourcing the managed defense and response requirements, leaving your in-house team free to continue focusing on the activities that support your business continuity.
Ardalyst can perform myriad functions, from a basic configuration of your optimal environment to a full implementation and sustainment strategy.
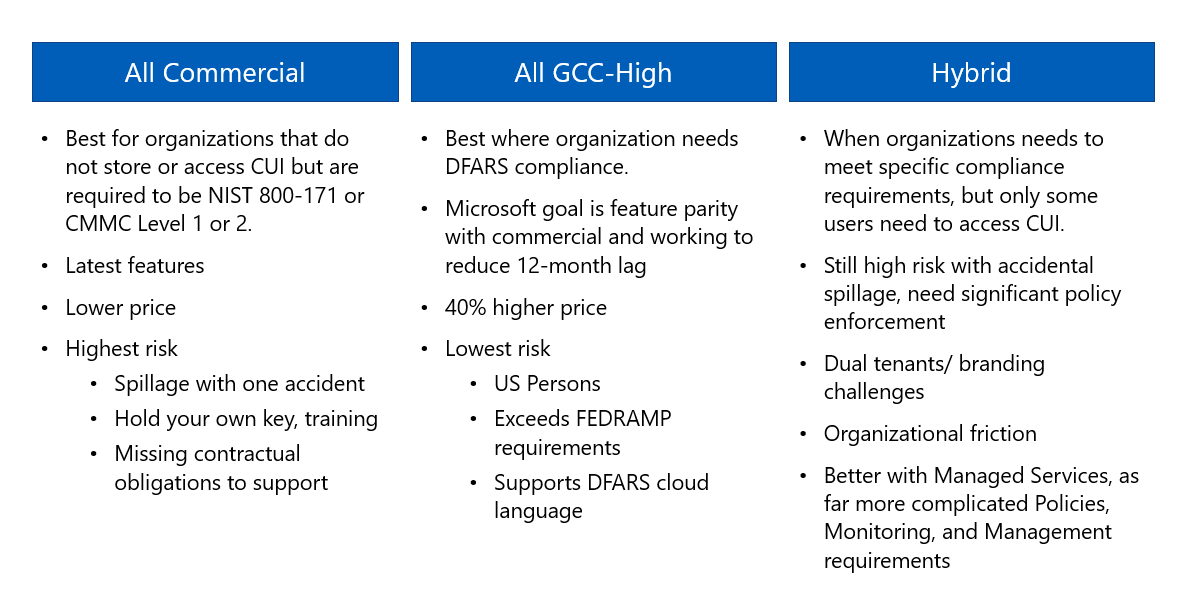
Step 5
Choose an Architecture
You have options. Choosing an architecture is largely determined by how many of your employees handle different types of information.
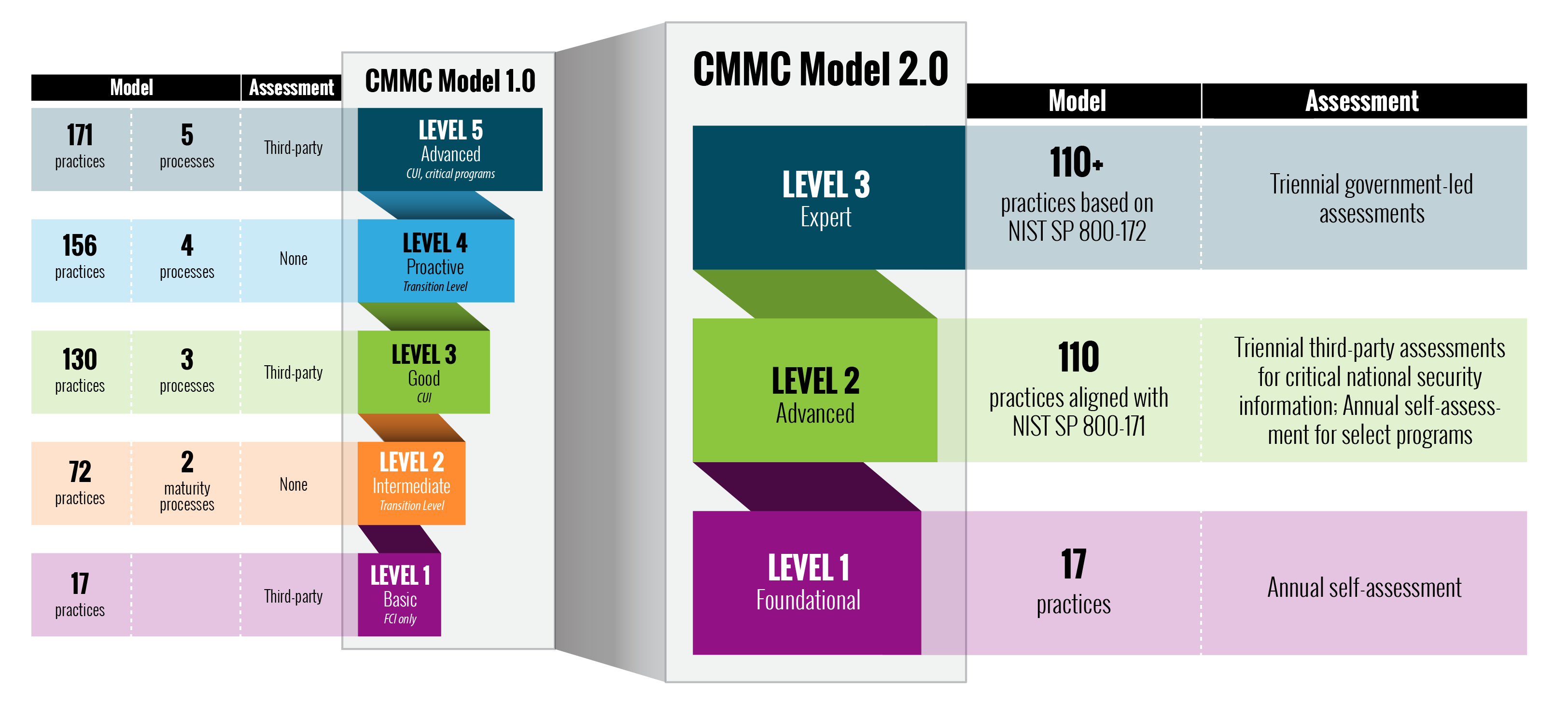
For example, the federal government’s Cybersecurity Maturity Model Certification (CMMC) states that an organization can achieve certification for the entire company or a smaller enclave of the company, depending on the number of users handling controlled unclassified information (CUI). This is especially good for smaller companies who only have a handful of employees handling CUI and don’t want to spend the money to put every employee on a platform that protects information they aren’t using. The CMMC Accreditation Body has yet to release any further guidance about how a segmented model will be evaluated, but it’s something companies should consider in advance, depending on what regulatory demands they must meet.