What is CMMC?
Overview of CMMC
CMMC, or the Cybersecurity Maturity Model Certification, is a comprehensive cybersecurity standard developed by the Department of Defense (DoD) specifically for businesses involved in government contracts. It aims to safeguard controlled unclassified information (CUI) from cyber threats, ensuring a higher level of security across the entire defense supply chain.
CUI refers to sensitive information that requires protection but is not classified under national security regulations. CUI can include technical drawings, research data, and personal information of military personnel. The loss or compromise of CUI can have serious consequences for national security, making its protection a top priority for the DoD.
The CMMC model combines various cybersecurity standards and best practices, such as those outlined in NIST SP 800-171, into a single, unified framework. It establishes a clear set of guidelines for defense contractors to follow, streamlining the process of implementing and maintaining effective security measures.
CMMC levels
The DoD initially released CMMC v1.0 in January 2020. However, using industry feedback, the DoD has since released the CMMC v2.0 revision in December 2021, taking the levels of certification from 5 (Level 1: Basic Cyber Hygiene to Level 5: Advanced) to 3 (Level 1: Foundational to Level 3: Expert).
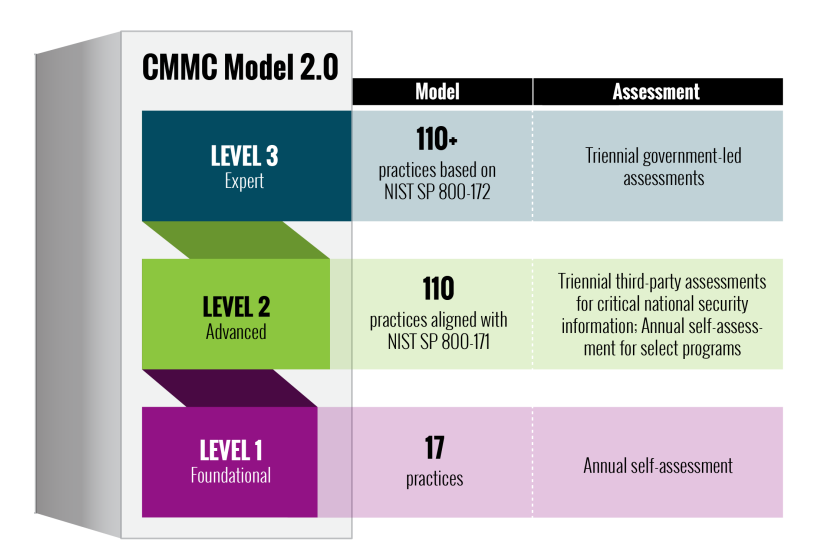
CMMC Level 1 – Foundational
Level 1, Foundational, remains similar to its counterpart in v1.0. It contains 17 practices required for companies that only handle Federal Contract Information (FCI) and do not handle Controlled Unclassified Information (CUI). This level requires companies to perform an annual self-assessment of their basic cyber hygiene.
CMMC Level 2 – Advanced
Level 2, Advanced, is similar to Level 3 in v1.0. It outlines 110 practices aligned with NIST SP 800-171 required by defense contractors that handle and must safeguard CUI. To achieve Level 2 certification, organizations must undergo triennial third-party assessments by organizations called Certified Third-Party Assessment Organizations, or C3PAOs. C3PAOs are certified by the CMMC Accreditation Body to perform assessments on behalf of the government to ensure compliance throughout the defense industry.
CMMC Level 3 – Expert
Level 3, Expert, is similar to Level 5 in v1.0. It includes the 110 practices in Level 2 and an additional set of practices based on NIST SP 800-172, which is currently in draft form. These requirements provide a greater depth of protection of critical national security information and reduce the risks of exploitation by Advanced Persistent Threats (APTs). At this level, organizations must undergo a triennial assessment of their cyber programs by the U.S. government.
Who needs CMMC?

As a prerequisite for bidding on DoD contracts, defense contractors who handle federal contract information (FCI) and/or controlled unclassified information (CUI) as part of their work with federal and state agencies are required to meet CMMC requirements. Compliance ensures eligibility for government contracts and demonstrates a commitment to protecting sensitive information.
The DFARS 252.204-7019 clause, which has been in effect since November 30, 2020, states that the contractor must comply with NIST 800-171 requirements, complete a self-assessment of their ability to meet those requirements resulting in a score that must then be submitted to the Suppliers Performance Risk System (SPRS), along with a System Security Plan (SSP) and a Plan of Action and Milestones (POAM). This means that whether your business seeks out an official assessment to be certified at CMMC level 2 or not, the requirements for your cybersecurity program remain the same.
What CMMC level do I need?
The level achieved by the contractor will determine contract eligibility. Most small companies that only handle Federal Contract Information (FCI) will only need Level 1 certification, but any company that handles Controlled Unclassified Information (CUI) will need at least Level 2. The DoD expects that organizations that currently meet DFARS requirements will be able to qualify for Level 2 with relative ease. However, based on government research, most organizations that self-certify overestimate their compliance and have work to do now to be ready for third-party verification.
How do I get CMMC certified?
Conduct your risk assessment to identify gaps
Great cybersecurity is not about checking off boxes, it’s about mitigating your risks. This starts with understanding where they are. Begin with assessing your risks at both an Organizational and a Technical level. This allows you to understand not just where the gaps are in your technology/coverage, but also your business goals to align your cybersecurity with how you do business.
Get a Free Risk Assessment! Start Your Free Trial Today!
Acquire tools & implement required controls
There are many tools to help you conduct business and protect CUI appropriately. For example, the Tesseract program is built on the Microsoft platform for its ability to help strengthen your cybersecurity baseline, control and protect data, and streamline compliance. Leveraging Microsoft consolidates the need for multiple tools by giving you access to both productivity tools and security capabilities to assist with satisfying multiple controls on the NIST/CMMC requirements list.
Regardless of the tool you choose for your program, once you have identified the gaps in your current security posture, you must configure your tools and implement the necessary controls to address the gaps in meeting CMMC requirements for your desired maturity level. This may include updating policies, procedures, and more.
Document your program
CMMC compliance involves thorough documentation of your cybersecurity processes and practices. Maintain up-to-date records that demonstrate your adherence to CMMC requirements, as these will be reviewed during the assessment process.
You’ll recall the DFARS 252.204-7019 clause currently states that the contractor must comply with NIST 800-171 requirements, including completing a self-assessment of their ability to meet those requirements to be submitted to the Suppliers Performance Risk System (SPRS), along with a System Security Plan (SSP) and a Plan of Action and Milestones (POAM).
Additional program documentation you’ll need includes:
Cybersecurity Program Manual: Outlines all the details of your cybersecurity practices, incident response protocols, and contains all the policies outlined in your cybersecurity program
Business-Specific Policies: Policies that tell your organization how to conduct business and sets the boundaries for what is acceptable and not. Your policies should be meticulously crafted to address your specific challenges from access control to incident response. This includes policies like BYOD(device), remote work, etc.
CUI Flow Diagram: Understanding the flow of Controlled Unclassified Information (CUI) within your organization is vital to maintaining confidentiality, integrity, and availability. A CUI Flow Diagram provides a clear visual representation of how CUI traverses your systems, including interaction points, and authorization boundaries.
Network Design Diagram: A visual representation of your network showing an intricate web of all your interconnected devices, servers, and systems that make up your network and how they interact.
Shared Responsibility Matrix: A comprehensive document that clearly defines the roles and responsibilities of each individual and department in your organization’s cybersecurity efforts.
Train your employees
Employee training plays an instrumental role in maintaining robust cybersecurity practices within an organization. In the context of CMMC compliance, it is paramount to ensure that your workforce understands not only the significance of adhering to CMMC requirements but also the specifics of the practices and policies set by your organization.
CMMC-compliant training should be comprehensive, covering all domains of the CMMC framework relevant to the employee’s role. This might include training on how to handle CUI, best practices for secure communication, guidelines for password management, and procedures to follow in case of a suspected security incident.
Training should be conducted regularly, not just as a one-time event. Cyber threats are constantly evolving, and employees need to stay up to date with the latest tactics used by cybercriminals. Regular training updates can ensure that employees remain vigilant and equipped with the latest knowledge to protect the organization’s data.
Engage a certified third-party assessor
A C3PAO, or certified third-party assessor organization, is integral to the CMMC model. Leveraging third-party assessors ensures an unbiased, comprehensive evaluation of a company’s cybersecurity practices.
C3PAOs are responsible for conducting an independent assessment of your adherence to the CMMC requirements specific to your targeted maturity level. This involves scrutinizing your cybersecurity policies, procedures, and systems to ascertain whether they meet the necessary criteria. The C3PAO must be certified by the CMMC Accreditation Body, ensuring they have the expertise and credentials to conduct these assessments accurately and professionally.
The assessment process involves several steps. Initially, the C3PAO will review the documentation of your cybersecurity practices and processes to understand their current posture. This is followed by an onsite visit to validate the implementation of these practices and processes. The C3PAO will interview relevant staff, observe operations, and inspect systems and networks to ensure the documented practices are effectively implemented.
Upon successful completion of the assessment, the C3PAO will submit an assessment report to the CMMC Accreditation Body, known as the CyberAB, outlining their findings and their recommendation for certification. Upon review and approval of this report, CyberAB will issue the appropriate certification, which remains valid for three years.
Begin your journey to CMMC compliance
Take advantage of our FREE Tesseract Program Trial including:
- A free Risk Assessment that meets the requirements for RA.L2-3.11.1 and lays the foundation for your program
- A preview of your System Security Plan (SSP) & Plan of Actions and Milestones (POAM)
- An overview of the Tesseract Managed Cybersecurity Program and your path to getting & staying compliant
- A technical design of your Tesseract program enclave
- Exclusive deals on additional tools like Microsoft GCC & GCC-High
Frequently asked CMMC questions
How is CMMC different from NIST SP 800-171?
While both CMMC and NIST SP 800-171 aim to protect CUI, CMMC introduces a certification process with three maturity levels, requiring businesses to undergo third-party assessments to verify compliance for most levels.
How long does CMMC certification last?
CMMC certification is valid for three years. After this period, businesses must undergo another assessment to maintain their certification.
Can SMBs achieve CMMC compliance without external assistance?
While it’s possible for SMBs to achieve compliance independently, leveraging the expertise of a managed security service provider (MSSP) or a cybersecurity consultant like a CMMC Registered Provider Organization (RPO) can simplify the process and provide valuable guidance.
How much does it cost to achieve CMMC compliance?
The cost of achieving CMMC compliance varies greatly, depending on the maturity level targeted, the size and complexity of the business, and the existing security measures in place. Costs may include employee training, technology upgrades, and fees for engaging a C3PAO.
What is a C3PAO?
A C3PAO, or Certified Third-Party Assessor Organization, is an entity certified by the CMMC Accreditation Body to conduct independent assessments of a company’s cybersecurity practices for CMMC certification.
Do all DoD contractors need to be CMMC certified?
Yes, all companies doing business with the DoD, including subcontractors, must achieve a certain level of CMMC certification based on the nature of their work and the sensitivity of the information they handle.
What happens if a business fails a CMMC assessment?
If a business fails a CMMC assessment, it will not receive certification and will need to address the identified gaps before requesting a re-assessment. This could impact the business’s eligibility for future DoD contracts. Tesseract includes an Assessment Guarantee. If (big if) you fail your assessment, your Tesseract team will address the gaps for you at no additional cost.
Can a business aim for a higher level of CMMC certification than required for a specific contract?
Yes, a business can aim for a higher level of certification. This could potentially make the business more competitive for future contracts that require a higher level of cybersecurity maturity.
Will CMMC requirements change over time?
CMMC is a dynamic framework, and its requirements may evolve over time to address emerging cyber threats and technologies. Organizations should stay informed about updates and changes to ensure ongoing compliance with the latest CMMC standards.
Does CMMC certification guarantee cybersecurity?
While CMMC certification provides a structured approach to cybersecurity and significantly reduces the risk of cyber threats, no certification can guarantee complete immunity from cyber attacks. It’s crucial for businesses to continually monitor and update their cybersecurity practices in response to evolving threats.