Initial Thoughts on CMMC v0.4
The Department of Defense (DoD) Undersecretary for Acquisition and Sustainment is developing a unified cybersecurity standard for DoD acquisitions, the Cybersecurity Maturity Management Certification (CMMC). With the recent release of version 0.4 of the draft framework, we have much more information to start planning ahead for this requirement, though changes are expected after review and feedback from industry. Here’s what we know so far.
- This certification builds upon existing standards set in the Defense Federal Acquisitions Regulation Supplement (DFARS) by adding additional focus on processes and policy.
- There are 5 possible levels of certification and ultimately, all Requests for Proposals (RFPs) issued by the government in the future will specify what level of certification a company must have in order to bid.
- The levels are cumulative, so at each level of certification all of the requirements of the previous levels must still be met to maintain certification.
- The certification adds a 3rd party verification system, eliminating the ability for organizations to self-certify compliance.
- The DoD expects CMMC to be in place in January of 2020.
- The DoD also recognizes that there is a cost associated with maintaining proper cybersecurity and as part of CMMC will allow contractors to include their cybersecurity expenses as an allowable cost in their contracts.
CMMC v0.4 is a significant volume to digest, with 380 new compliance requirements and four domains added to the 14 existing domains NIST 800-171 already required. Within each domain are technical processes and practices that companies will need to follow in order to remain compliant at each of the 5 levels. This framework requires organizations to change the way their current policies align. New policies will need to be drafted to meet the demands of this 18-domain construct.
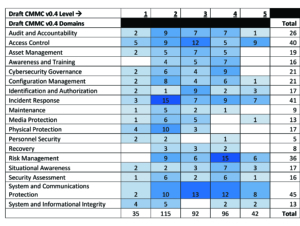
In talking with other government contractors, we understand some of the initial concerns that CMMC burdens organizations with a significant and costly amount of work, and we’ve begun deconstructing each of the domains to build a process to make it easier to digest. We believe DoD contractors should take three steps to prepare for CMMC:
- Organizations should start now to ensure they meet existing DFARS and ITAR requirements, including NIST 800-171. This includes evaluating their existing security controls as well as monitoring and response capabilities.
- Contractors should implement solutions based on upcoming requirements, including ensuring that their policies are backed up by documented, verifiable processes and procedures.
- Contractors must put in place, either internally or via managed service providers, the capability necessary to defend against attacks.
We noted several areas of v0.4 that included more detail on the types of security capabilities the DoD desires of its DIB partners’ cyber systems. Looking at these practices from an attacker’s perspective, our analysts feel this framework makes an excellent effort to identify what a defense contracting organization needs to implement to defend against nation-state adversaries. Overall, we felt CMMC v0.4 was a step in the right in direction to mature organizations’ cyber security posture. We expect future iterations of this product to further expand on the maturity domain and lexicon used throughout the document.





