What the Latest DFARS Rule Changes Mean for You
This week the DoD released the interim final rule for the Cybersecurity Maturity Model Certification (CMMC) and added details that may have immediate effects.
It is outlined in an 89-page notice in the federal register published yesterday (Sept 29) entitled “Defense Federal Acquisition Regulation Supplement: Assessing Contractor Implementation of Cybersecurity Requirements (DFARS Case 2019-D041).”
What does this mean? In essence, the DoD is implementing what may be two substantive changes as to how an organization in the Defense Industrial Base (DIB) will demonstrate their compliance with the DoD’s regulation for cybersecurity starting as soon as November 2020.
- CMMC has been coming for a while, and it will now have an official DFARS Clause (252.204-7021) implementing a phased rollout until September 30, 2025.
- In the meantime, this change also brings with it two additional changes intended to “motivate defense contractors and subcontractors who have not yet implemented existing NIST SP 800-171 security requirements to take action to implement the security requirements on covered information systems that process Controlled Unclassified Information (CUI) , in order to protect our national and economic security interests.”
These two changes to how DFARS 7012 required NIST SP 800-171 will now be assessed:
- DFARS Provision 7019, “Notice of NIST SP 800-171 DoD Assessment Requirements,” will require companies to have at least a NIST SP 800-171 Basic Assessment on record with the DoD to be considered for award.
- DFARS Clause 7020 will require contractors to grant access to their facilities, systems, and personnel for the government to run Medium or High Assessments.
It is critical to not confuse these changes. The bottom line on CMMC and the future of cyber readiness in the DoD constellation of defense contractor satellites is that the days of taking risk with cybersecurity are over. Now that this interim rule has been formally published, the general public has 60 days to comment. Katie Arrington, DoD’s CISO for Acquisition and Sustainment and chief CMMC official, previously stated on the record that the rule-making process would wrap up by the end of 2020. This step falls in cadence with that timeline and every organization in the DIB should be examining their strategy for cybersecurity going forward.
How do we evaluate these changes?
In the short-term, it has gotten more painful to be non-compliant.
The notice breaks down three types of assessments all organizations should expect to see starting in as soon as 60 days with DFARS 7019 and 7020:
- DFARS Provision 7019 (starting as soon as November 30, 2020) will advise offerors they will need to have a current (i.e., not older than three years) NIST 800-171 assessment on record in the Supplier Performance Risk System (SPRS). Contracting officers will be required to verify each company’s Summary Level Score (an up to 110 point score derived from the NIST SP 800-171 DoD Assessment Methodology) prior to awarding a contract, task order, or delivery order as well as exercising an option year or extending the period of performance for a contract. This provision will be phased in over the next three years as new contracts are released and old contracts age out. There will be three types of assessments:
- Basic Assessment: an estimated 30-minute self-assessment using the organization’s existing System Security Plan (SSP) and Plan of Actions and Milestones (POAM) to calculate their own score and then entering it on SPRS. The SPRS entry will consist of six fields: SSP name, CAGE code associated with the plan, a brief description of the plan architecture, date of the assessment, total score, and the date a score of 110 will be achieved. If you already have an SSP and POAM, it should take less than an hour to complete the Basic Assessment.
- Medium Assessment: The DoD estimates that 200 unique organizations will go through a Medium Assessment each year, based on the need for a medium level of confidence in how the organization is handling CUI. It will require a DoD representative, most likely from the Defense Contract Management Agency (DCMA) Defense Industrial Base Cybersecurity Assessment Center (DIBCAC), onsite at the organization’s facilities conducting a review of their Basic Assessment, a thorough document review, and holding discussions with the contractor to obtain additional information or clarification as needed.
- High Assessment: The DoD estimates that 110 unique organizations will go through a High Assessment each year. It will be similar to the Medium Assessment, with the addition of the government performing “verification, examination, and demonstration” of the SSP to validate that NIST SP 800-171 security requirements have been implemented as described.
- Clause 7020 “NIST SP 800-171 DoD Assessment Requirements” will add on to Provision 7019 by requiring a contractor to provide the Government with access to its facilities, systems and personnel when it is necessary for the DoD to conduct an assessment as well as make sure their subs have submitted their Assessments to SPRS prior to awarding a subcontract.
While the rapid onset of additional NIST SP 800-171 compliance rules may seem daunting, it doesn’t have to be hard or expensive to achieve the readiness required by the new rule. We recommend that organizations take a formalized and structured approach to their cybersecurity posture and consider three significant points about the importance of their investment:
- Cybersecurity is shifting from being an acceptable business risk to a potential business advantage. On Tuesday, Politico called CMMC “one of the biggest changes ever made to the Defense Industrial Base.” The announcement of this interim rule preceded by the announcement of CMMC pathfinders and the official certification of CMMC assessors in the past two weeks is yet another sign of the significance of the program and its importance in the future of contracting with the DoD.
- Operational vs. Capital Expenditures. As you are looking to make investments to ensure you have a perfect score on your new Basic Assessment for each of your SSPs, favor operational expenditures over capital expenditures. Contracts with CMMC requirements are expected to make cybersecurity an allowable cost, and those costs are expected to be used to assess whether you are investing enough for the appropriate level of maturity. Large capital expenditures now may make it harder to tie those costs to specific projects. Look for providers that can provide those capabilities as a service.
- NIST SP 800-171 compliance does not equal a mature cybersecurity program. The notice clearly states “the current security requirements specified in NIST SP 800-171 per DFARS clause 252.204-7012, do not sufficiently address additional threats to include Advanced Persistent Threats (APTs).” If you need to be NIST SP 800-171 compliant now, then you will want to strategically consider the additional capabilities required for CMMC Level 3. Furthermore, both the High Assessment under DFARS 7019 and the CMMC Assessment under DFARS 7021 will require demonstrating the maturity of your operation of the underlying controls. CMMC will also require you to “say what you do and do what you say” by documenting your practices and demonstrating to a Certified Assessor that you follow your documentation.
Given DFARS Provision 7019 and Clause 7020, CMMC cannot come fast enough!
DFARS Clause 7021 “Cybersecurity Maturity Model Certification Requirements” will phase CMMC into contracts over the next 5 years. Inclusion of a CMMC requirement in a solicitation during this time period will be controlled by the USD(A&S). Contracts with CMMC language will require the contractor to:
- maintain the requisite CMMC level for the duration of the contract.
- ensure that its subcontractors also have the appropriate CMMC level prior to awarding a subcontract or other contractual instruments.
- include the requirements of the clause in all subcontracts or other contractual instruments.
CMMC is meant to build upon the “assessment methodology” for 800-171, the notice says, through adding the requirement for “a comprehensive and scalable certification element to verify the implementation of processes and practices associated with the achievement of a cybersecurity maturity level. CMMC is designed to provide increased assurance to the Department that a DIB contractor can adequately protect sensitive unclassified information such as Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) at a level commensurate with the risk, accounting for information flow down to its subcontractors in a multi-tier supply chain.”
CMMC Assessments will be conducted by Certified Third Party Assessment Organizations (C3PAOs), which are accredited by the CMMC-Accreditation Body (AB). C3PAOs will provide CMMC Assessment reports to the CMMC-AB who will then maintain and store these reports in appropriate database(s). The CMMC-AB will issue CMMC certificates upon the resolution of any disputes or anomalies during the conduct of the assessment. These CMMC certificates will be distributed to the DIB contractor and the requisite information will be posted in SPRS.
If a contractor disputes the outcome of a C3PAO assessment, the contractor may submit a dispute adjudication request to the CMMC-AB along with supporting information related to claimed errors, malfeasance, or ethical lapses by the C3PAO. The CMMC-AB will follow a formal process to review the adjudication request and provide a preliminary evaluation to the contractor and C3PAO. If the contractor does not accept the CMMC-AB preliminary finding, the contractor may request an additional assessment by the CMMC-AB staff.
In the notice, the DoD says, “The NIST SP 800-171 DoD Assessment and CMMC assessments will not duplicate efforts from each assessment, or any other DoD assessment, except for rare circumstances when a re-assessment may be necessary, such as, but not limited to, when cybersecurity risks, threats, or awareness have changed, requiring a re-assessment to ensure current compliance.” It is not clear how an organization that had a NIST SP 800-171 High Assessment may need or not need a CMMC assessment in the next three years. Although a CMMC Level 3 assessment is the first CMMC level to cover all 110 NIST 800-171 controls, it has an additional 20 practices and 3 processes that would not be covered. This is explained well in the following table from the notice:
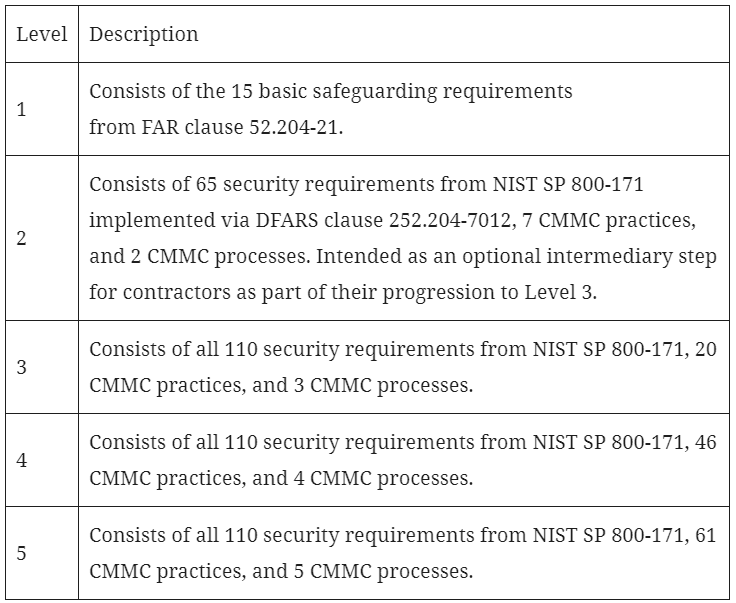
These new rules outlining how proposals will be assessed and awarded illustrate the seriousness with which CMMC is being treated within the DoD. Organizational leaders should consider pursuing CMMC accreditation now to be ready as soon as possible after the rollout 60 days from now. We recommend that organizations take a strategic approach to assess their current cybersecurity strategy and consider four significant points about the importance of their investment:
- CMMC standards should help reduce cybersecurity investment costs, and the government is willing to pay for that. The U.S. government is losing $600 billion a year because of data loss. CMMC demonstrates the DoD’s motivation and willingness to help companies recoup their investment in cybersecurity. Ms. Arrington has backed this up in numerous interviews and webinars: “We understand that there’s going to be a cost to this, but when we’re losing $600 billion a year, if I have to put $1 billion in to make sure that we protect ourselves, it’s a huge return on investment,” she said. “More importantly, [we’re] investing in ensuring our supply chain remains whole.” The DoD will allow contractors to include the costs of cybersecurity in the rates they charge the department. It is not clear on what will be allowed, we expect this to be worked out through the initial contracts. The way we understand it will work is that offerors will include those costs in their proposals to meet the CMMC Levels required in the Requests for Proposals (RFP). Those proposed costs will then be judged on sufficiency (are they charging too little/too much to meet the CMMC Level required) and part of the scoring criteria for selection.
- Companies are choosing to make cybersecurity a competitive advantage. We are already seeing a trend in early adopters where they are racing to not just meet CMMC Levels but exceed them. At the recent Gartner Security and Risk Management Summit, VP Analyst Katell Thielemann discussed how CMMC is disrupting contract capture strategies, noting “Arms Race to 5op tier primes are sending out self-evaluation surveys to their supply chain and cutting out subcontractors that will not let them rapidly get to CMMC Level 5.
- Consider a different program strategy for CMMC as you move away from a program based on just NIST SP 800-171 compliance. As offerors will be judged on their costs to meet certain levels, we expect there to be several strategies for how organizations will meet this new opportunity. Where NIST SP 800-171 is focused on compliance of a system, CMMC is focused on the maturity of the organization. The maturity model itself allows DIB contractors to “achieve a specific CMMC level for its entire enterprise network or particular segment(s) or enclave(s), depending upon where the information to be protected is processed, stored, or transmitted.” Making your whole organization Level 5 certified may or may not make sense for your capture and investment strategies. Leveraging outside managed security service providers that understand CMMC to enable a hybrid approach may give you considerable advantage.
- Achieving cyber maturity makes your business stronger. Having a robust cyber program makes your organization more productive and more resilient. Ardalyst customers have stated that without the move to modern secure platforms, COVID closures would have caught them flat footed, instead they have been thriving. Your investment can do double duty – meeting compliance requirements for bidding on and receiving federal government contracts while making your business better. CMMC is a maturity model to help the DIB better safeguard our national security, which is in everyone’s best interest. It is simply the right thing to do for our nation.
We are here to replace uncertainty with understanding.
With these rule changes, DIB organizations will need to evaluate these data points and get moving on their compliance measures with NIST SP 800-171, as well as develop their CMMC strategy.
Ardalyst can ensure you have the resources and information you need in your journey to cyber readiness. Our “Govern” services ensure your organization is doing the right things to develop and maintain up-to-date policies and procedures that help you maintain compliance with changing regulations. From there, you can choose from a variety of options to “Harden” your posture by implementing capabilities that reduce your vulnerabilities and make it difficult for the adversary to access and compromise your environment and “Defend” your networks by leveraging tools that increase your knowledge of threats and help your organization rapidly identify and respond to them. Contact Ardalyst for more information and assistance. We offer a free introductory Risk Management workshop, which is specifically designed to meet the anticipated requirements of CMMC Practice RM.2.141 and start clients on their CMMC journey today. Schedule a free consultation to get started.






