The CMMC Program Rule is Final: What It Means for Defense Contractors
The Department of Defense (DoD) has officially released the Final CMMC Rule, signaling a major step forward in securing the defense supply chain. The Cybersecurity Maturity Model Certification (CMMC) aims to ensure that contractors handling Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) adopt stringent cybersecurity practices to protect sensitive data from evolving cyber threats. With the final rule in effect, defense contractors and subcontractors must understand the key requirements and how to navigate the path to compliance.
This blog will break down the major developments of the Final CMMC Rule and what it means for your business. Plus, we’ll recap insights from our recent webinar, “The Final CMMC Rule Unveiled: How to Get and Stay Compliant,” and explain how to get started with your CMMC compliance today.
Key Developments in the Final CMMC Rule
1. Phased Implementation of CMMC
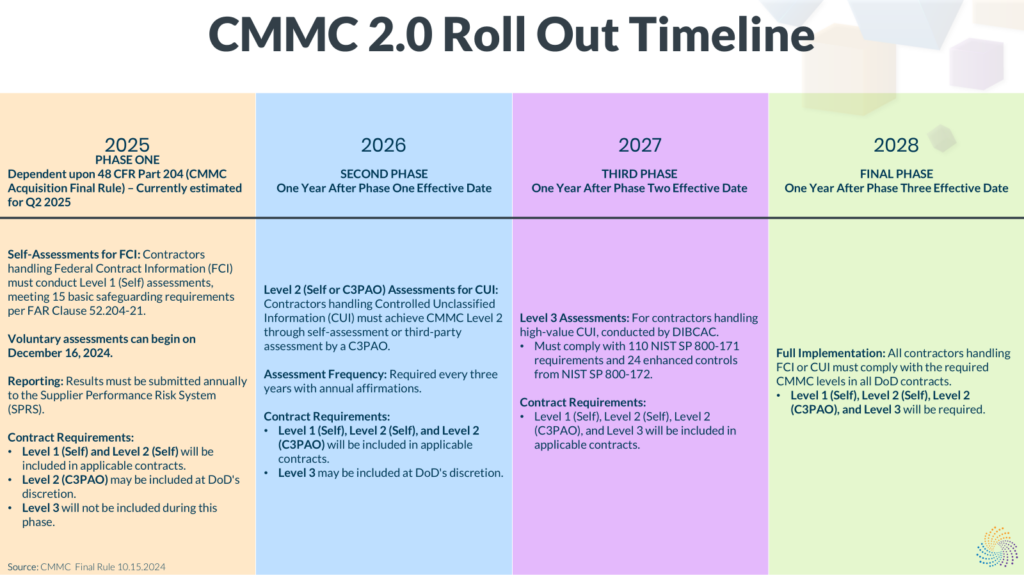
The Final CMMC Rule outlines a phased implementation timeline over the next several years. This staggered approach provides contractors the necessary time to achieve compliance without causing disruption to their eligibility for contract awards. The four phases are as follows:
- Phase 1 (Expected Start: Q2 2025): Contractors handling FCI must conduct Level 1 (Self) assessments, adhering to the 15 basic safeguarding requirements outlined in FAR Clause 52.204-21. These assessments are self-conducted and must be reported annually to the Supplier Performance Risk System (SPRS). For contractors handling CUI, Level 2 (Self) or Level 2 (C3PAO) assessments may be required based on contract specifications. [Source: 83095]
- Phase 2 (One Year After Phase 1): Contractors handling CUI must achieve Level 2 certification, either through self-assessment or by undergoing a third-party C3PAO assessment. Contractors are required to undergo an assessment every three years and provide annual affirmations of compliance. [Source: 83095]
- Phase 3 (One Year After Phase 2): Contractors handling high-value CUI will need to achieve Level 3 certification, which incorporates the 110 security controls from NIST SP 800-171 and an additional 24 enhanced security requirements from NIST SP 800-172. Level 3 assessments will be conducted by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC). [Source: 83095-83096]
- Phase 4 (One Year After Phase 3): Full implementation will require all contractors handling FCI or CUI to comply with the relevant CMMC level for their contracts. CMMC requirements will be mandatory across all DoD solicitations, including option periods on existing contracts. [Source: 83096]
2. Understanding CMMC Levels
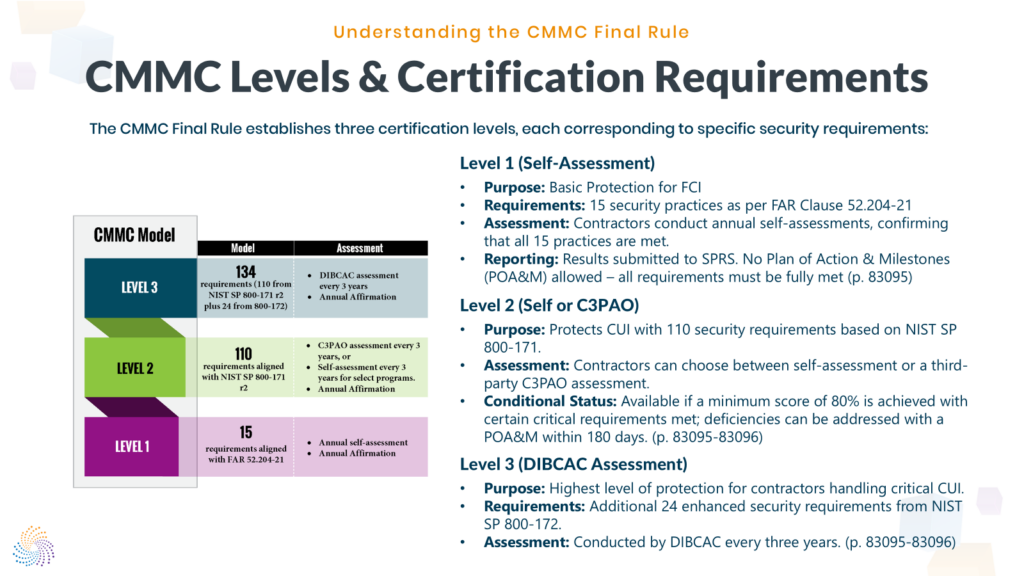
The CMMC framework is structured with three distinct levels, each targeting different types of information and requiring increasingly stringent cybersecurity practices:
- Level 1 (Self): Designed to protect FCI, this level focuses on 15 basic security practices as per FAR Clause 52.204-21. These are self-assessments and must be conducted annually, with results reported to SPRS. [Source: 83095]
- Level 2 (Self or C3PAO): Contractors handling CUI must comply with the 110 security controls from NIST SP 800-171. Depending on contract specifications, contractors may either conduct a self-assessment or undergo a third-party assessment by a C3PAO. Contractors can receive conditional certification if they meet 80% of the controls, with a Plan of Action & Milestones (POA&M) to address unmet requirements. [Source: 83095]
- Level 3 (DIBCAC): Contractors handling high-value CUI or critical systems must implement the 110 controls from NIST SP 800-171 and 24 additional controls from NIST SP 800-172. Level 3 assessments are conducted by DIBCAC and focus on contractors managing more sensitive information and systems. [Source: 83096]
3. Critical Controls That Cannot Be Deferred

Certain critical cybersecurity controls must be fully implemented before a contractor can receive CMMC certification. These controls, which cannot be deferred through a POA&M, include:
- Access Control: Ensuring that external connections and public information handling are tightly controlled (AC.L2-3.1.20, AC.L2-3.1.22).
- Incident Response: Establishing robust detection, reporting, and mitigation processes.
- Encryption: Protecting sensitive data during transmission and while at rest.
- Multi-Factor Authentication (MFA): Enhancing access verification to safeguard systems from unauthorized access.
Other non-deferrable controls include managing physical access logs, escorting visitors, and monitoring external connections. [Source: 83096, 83235]
4. Plan of Action and Milestones (POA&M) Flexibility
The Final CMMC Rule offers contractors flexibility through the POA&M mechanism. If a contractor meets 80% of the required controls, they can still achieve conditional certification while addressing the remaining controls within 180 days. However, it’s important to note that certain critical controls, such as those related to access control, encryption, and MFA, cannot be deferred and must be fully implemented for certification. [Source: 83096]
5. Scoping and Asset Management

Contractors must carefully define the scope of their CMMC assessments, ensuring that all assets that process, store, or transmit FCI or CUI are included. These assets fall into categories like CUI Assets, Security Protection Assets, and Contractor Risk Managed Assets (CRMAs). Proper documentation through the System Security Plan (SSP) and an asset inventory is crucial for compliance, as these documents will be closely evaluated during assessments. [Source: 83232, 83235]
6. Continuous Monitoring and Reassessments

The Final CMMC Rule stresses the importance of continuous monitoring to maintain compliance. Contractors are required to affirm compliance annually and conduct full assessments every three years. Trigger events that may prompt reassessments include system architecture changes, significant security incidents, or emerging threats. Contractors must also maintain up-to-date security practices throughout the contract period. [Source: 83199-83200]
Stay Ahead with CMMC Compliance: Watch Our Webinar
The Final CMMC Rule is a game-changer for the defense industry, and staying compliant is essential for securing or renewing contracts with the DoD. To help contractors navigate the intricacies of the new rule, we recently hosted a webinar, “The Final CMMC Rule Unveiled: How to Get and Stay Compliant.” This session breaks down the key changes, how they impact your business, and practical steps for meeting CMMC requirements. Missed the webinar? Watch the replay now for a full overview!
Get Started on Your CMMC Compliance Journey Today
Compliance with the Final CMMC Rule is no longer optional. Whether your business handles FCI, CUI, or high-value CUI, it’s time to take action. At Ardalyst, we’re here to guide you through the process with our comprehensive Tesseract program, designed to make your compliance journey straightforward and efficient.
Ready to get started? Book a free trial of Tesseract today and take the first step toward ensuring your business stays compliant with the Final CMMC Rule.
Stay compliant. Stay competitive. Start your CMMC journey with Tesseract now!






