Five Steps to Building Your CMMC Strategy
The time to get CMMC compliant is now! Stacy Bostjanick, the Department of Defense’s Chief Information Officer, announced that they are eyeing March 2023 for the release of CMMC 2.0, and the DoD would begin implementing CMMC in contracts as early as May 2023. Depending on where you are in your compliance journey, this leaves less than a year to establish and document policies and procedures, purchase the necessary software, configure your networks, and prepare for CMMC audits. It’s time to get to work. Our five-step approach helps contractors develop a comprehensive plan for achieving CMMC compliance and staying compliant.

Determine Your Long-Term Strategy
What CMMC Level do you Hope to Ultimately Achieve?
CMMC, or the Cybersecurity Maturity Model Certification, consists of three levels.
Level 1 – Foundational: Contains 17 practices aligned with FAR 52.204-21 and is required for companies that only handle Federal Contract Information (FCI) and do not handle Controlled Unclassified Information (CUI).
Assessment: Level 1 only requires businesses to perform an annual self-assessment.
Level 2 – Advanced: Contains 110 practices aligned with NIST SP 800-171 required by defense contractors who handle and must safeguard CUI.
Assessment: Level 2 requires a triennial third-party assessment by a Certified Third-Party Assessment Organization or C3PAO.
Level 3 – Expert: Contains the same 110 practices of CMMC 2.0 Level 2 and adds controls from NIST SP 800-172 demonstrating a greater depth of protection of critical national security information and reducing the risks of exploitation by Advanced Persistent Threats (APTs).
Assessment: Level 3 requires a triennial assessment by the U.S. government. Assessments will be conducted by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
Determining the CMMC level you would like to ultimately achieve will help you make the proper strategic steps to get there in a way that works for your business.

Take the First Step
Do you want to take multiple steps or implement all at once?
Now that you know where you would like to be, you must determine the speed that’s right for you. For example, while you may hope to reach CMMC Level 2 compliance in the future, you may find that is better and more cost-effective for your business to achieve CMMC Level 1, or FAR 52.204-21 compliance (required of all federal contractors) now, and develop a System Security Plan (SSP) and Plan of Action and Milestones (POAM) for how you’d like to achieve CMMC Level 2 compliance later. Taking this approach will lay out a clearly defined roadmap of the next steps to ensure you reach your CMMC Level 2 goals. Some see early adoption as a competitive advantage. Others want to take multiple steps to reduce the pace of organizational change or spread out the costs. Figure out how important speed is to your strategy and your budget so you can identify the right steps and plan accordingly.

Identify the Scope
What systems and data do you need to protect?
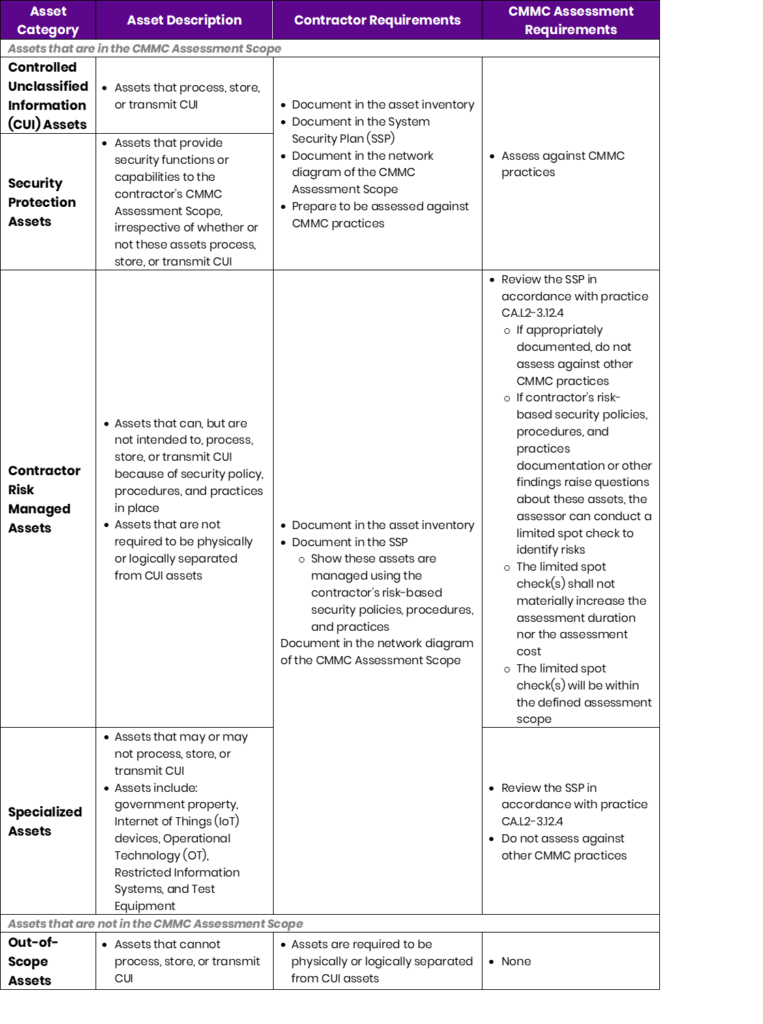
You have to understand what it is you must protect. The CMMC Scoping Guides are a great place to start. These guides provide information on what is in scope for a CMMC assessment. Keep in mind that assets that don’t process, store, or transmit CUI aren’t necessarily out of scope for CMMC Level 2 and Contractor Risk Managed Assets and Specialized Assets are still part of your System Security Plan (SSP) and require protection. After reviewing the scoping guide for your desired CMMC Level, determine where your value is, and make sure you’re building a program to defend it.

Assessing Your Technology
What technology should you adopt?
Understand your technology environment. You may have a state-of-the-art network that is ready to implement your security controls, but if you’re like most companies, cybersecurity requirements will be a big driver in upgrading your infrastructure or moving to the cloud. Cloud implementations are often easier to protect than on-premise and there are plenty of productivity improvements to be gained from moving to modern collaboration tools. Traditionally, on-premise solutions, referring to servers and data centers located in your office or business location, incur higher costs to get compliant because they require a more customized solution. With customization comes the need for more expertise, more configuration, and potentially more support during an audit. Therefore, choose new technologies based on your security and business goals. Keep in mind that the location of your infrastructure will play a huge role in how you secure it, develop your policies and procedures around it, and get and maintain your compliance.

Determine Your Resource Needs
What resources do you need?
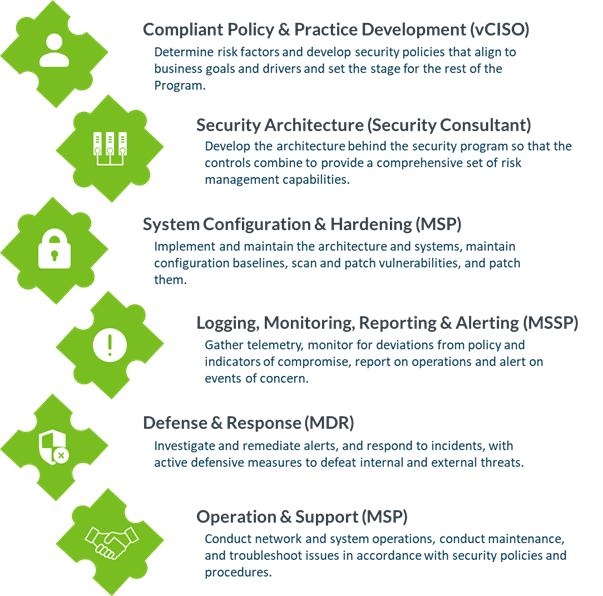
There are many pieces to an effective and compliant cybersecurity program, and that usually means pulling resources together like a Managed Security Service Provider (MSSP), Managed Service Provider (MSP), Managed Defense & Response (MDR), Compliance Consulting Services (vCISO), and Compliance Management Software. While some larger organizations may be able to support these functions with internal staffing, many small to mid-sized businesses don’t readily have this expertise on hand and the cost of salaries to obtain it can be out of reach. Determining up front what parts of your cybersecurity program you’ll be able to support on your own and what partners or resources you’ll need along the way is key to developing an effective and actionable plan for achieving your CMMC compliance.
You’ll also want to keep in mind how these resources will impact your budget. Vendor costs can run anywhere from $35,000-$250,000, MSSP services from $150,000-$300,000 for vCISO and Compliance Consultant services, MDR services from $82,000-$178,000, and MSP services from $120,000-$150,000. If these price tags feel way out of reach, you’re not alone. Check out our Tesseract Managed Cybersecurity Programs. Tesseract was designed by cybersecurity and compliance experts to make FAR 52.204-21, NIST 800-171, and CMMC simple and affordable. With three program options and four service packages, the result is a cybersecurity program that not only feels customized to your business but is faster, simpler, and more affordable than the alternatives.
Getting Started!
Building your CMMC strategy is no small feat. Knowing the right questions to ask, where you can save costs without compromising your security, and what the right steps are for your unique business is a challenge. Our team of CMMC-AB Registered Partitioners has helped numerous businesses not only determine the strategy that works for them but helped them execute that strategy to deliver comprehensive cybersecurity programs that meet their budget and return their confidence. It all starts with a free risk assessment & consultation. Contact us online at www.ardalyst.com, email us at info@ardalyst.com, or call us at (833) 682-8270 to schedule your free consultation today and let us help you build your CMMC strategy.






