On November 4, the Defense Department announced significant changes to its Cybersecurity Maturity Model Certification (CMMC) program with plans to eliminate third-party certifications for the lowest level of assessment, add a method for resolving assessment issues, and initiate new rulemaking efforts, among other changes. CMMC 2.0 maintains the program’s original goal of protecting sensitive information but builds on the initial framework to enhance Defense Industrial Base (DIB) cybersecurity against evolving threats. Under the CMMC program, DIB contractors will still be required to implement certain cybersecurity protection standards, and as required, obtain CMMC compliance as a condition of DoD contract award.
Key CMMC 2.0 Changes
Here are some key changes the release has brought about:
- Increased leadership accountability and liability. Business leaders will still be expected to reach compliance, but there will be more of a legal onus on individuals to comply without government interface.
- Increased enforcement actions by the government. While still being expected to reach compliance, the government will firmly address failures to meet current NIST standards. For example, your previously submitted POAM still matters.
- More streamlined requirements and assessments, thus making the entirety of the compliance journey possibly faster and more user-friendly.
Although the changes reflected in CMMC 2.0 mean that level 1 contractors are no longer required to seek third-party assessments, many DoD contractors lack the resources to complete their own self-assessments. Check out Ardalyst’s free self-assessment tool to understand where you stand on your path to compliance.
This update has also resulted in a reduction in the number of security compliance levels from five to three. This change eliminated former levels two and four and has resulted in the new tiered model structured as follows: Level 1 ‘foundational’, Level 2 ‘advanced’, and Level 3 ‘expert.’
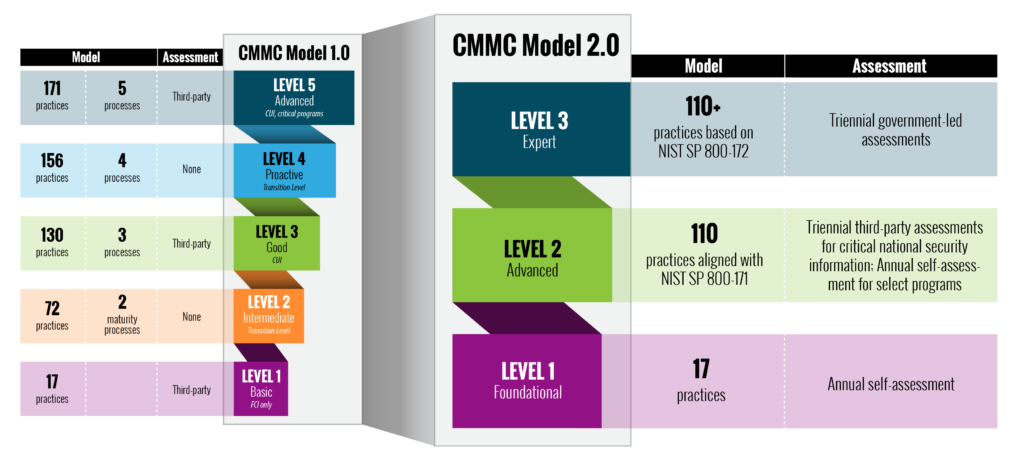
Level 1 will include 17 practices and allow for annual self-assessments.
Level 2 will include 110 practices alighted with NIST SP 800-171 and require triannual third-party assessment for critical national security information. Annual self-assessments will be granted for select programs.
Level 3 will include more than 110 practices based on NIST SP 800-172 and will require triannual government-led assessments.
What Happens Next?
Seeking out and attaining CMMC compliance is still a strategic decision that improves your organization’s cybersecurity in a programmatic way. With CMMC, organizations still need to meet NIST 800-171. They still need an SSP and a POAM. They still need to calculate a score and record it in SPRS and update it every year. POAMs also need to have a “clearly defined timeline.”

Looking for more recommendations and next steps? Watch the “CMMC 2.0 Masterclass: Where We Go From Here” webinar replay to hear from cybersecurity and CMMC-subject matter experts, Michael Speca, Josh O’Sullivan, and Robert Metzger.
Whether you have started on the path to compliance, or you are just getting started, CMMC 2.0 is not a big change. Our best advice is stop stalling and get started! Ardalyst has the tools to help you on your road to compliance. Schedule your free consultation to see where you stand with CMMC 2.0 and begin your journey today.






