Breaking Down Zero Trust Architecture and Exploring Its Gaps
Only two years into the new decade and our nation has been faced with increasing operational challenges. The pandemic turned us into a “remote-first world” making us more digitally dependent than we’ve ever been. As we’ve made this digital shift, we’ve also seen our traditional cybersecurity perimeters do the same to account for cloud solutions and disparately located employees outside of the traditional perimeter. This created the perfect opportunity for our adversaries and led to some significant cyber events, like the SolarWinds and Colonial Pipeline exploitations. Practitioners, organizational and national leaders agree, we must do something to improve the standard of cybersecurity across our nation to prevent these attacks. Zero Trust is one solution.
What is Zero Trust Architecture (ZTA)?
The National Institute of Standards and Technology (NIST) defines Zero Trust Architectures as “an enterprise cybersecurity architecture that is based on Zero Trust principles and designed to prevent data breaches and limit internal lateral movement.” In other words, assume that untrusted users already exist inside and outside the network, so trust can never be implicitly assumed or granted – it must be continually evaluated.
Zero Trust Principles
Microsoft, the industry’s leader in Zero Trust solutions, outlines Zero Trust principles as:
1. Verify Explicitly — Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
2. Use least privileged access — Limit user access with just-in-time and just-enough-access (JIT/JEA), risk-based adaptive policies, and data protection to help secure both data and productivity.
3. Assume Breach — Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
Where did all the ZTA Buzz Come From?
In response to the new normal (the current rise in outsized cyber-attacks), Executive Order 14028 set a new standard for the practice of cybersecurity inside and outside of government. The scope of the EO is to cover the protection and security of “systems that process data” (i.e., Information Technology (IT)) and “those that run the vital machinery that ensures our safety” (i.e., Operational Technology (OT)). It sets out to remove barriers to sharing threat information; standardize and consolidate the conduct of vulnerability management, incident response, and threat hunting practices within the government; and modernize federal infrastructure and government cybersecurity architectural standards to shift away from an on-premises, perimeter-based strategy to a cloud-based, Zero Trust Architecture (ZTA).
What’s the Catch?
In an ideal world, a true Zero Trust cybersecurity system could be the only cybersecurity system you need, as you are collecting all the data and using it to make every access decision. In practice, this requires extensive data collection, curation, and analysis. Driving accurate decisions on every interaction can be messy, inefficient, and impractical, especially when adversaries exploit the underlying dependencies. Always remember, the adversary gets a vote. This doesn’t mean Zero Trust is without merit, only that it should not be your sole cybersecurity strategy.
Understanding the Gaps in a Zero Trust Architecture
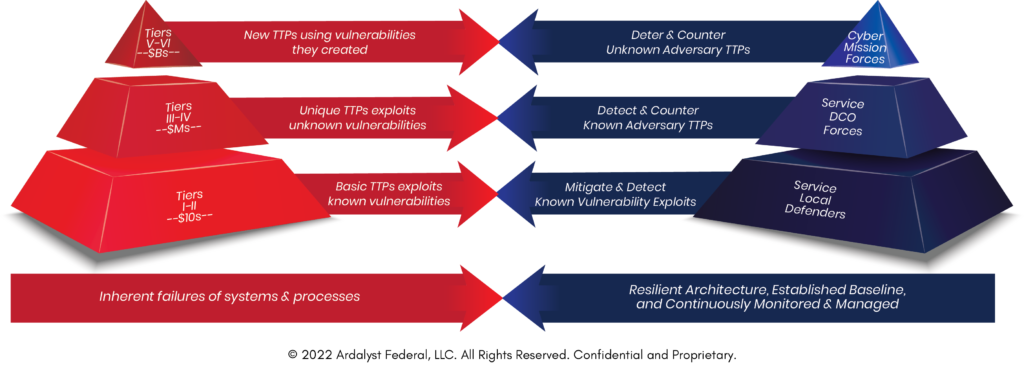
Thriving (let alone surviving) in the new normal requires organizations to have strategies to detect and respond in the “All-Threat” operating environment (i.e., collectively and continuously challenged by all four tiers of cyber threats), specifically:
- No Adversary: Situations when there is no adversary or intent to purposely cause a cyber event (e.g., Natural Disasters).
- Low-Tier: Spends tens of dollars to use known adversary tactics, techniques, and procedures (TTPs) to exploit pre-existing known vulnerabilities.
- Mid-Tier: Spends millions to use known TTPs to find and exploit unknown vulnerabilities.
- High-Tier: Spends billions to create new TTPs with new vulnerabilities for their targeted use.
| Low-Tier Threats Known Knowns | Mid-Tier Threats Known Unknowns | High-Tier Threats Unknown Unknowns |
| Low-Tier adversaries use publicly available tools and scripts with well-known, basic TTPs that cost in the tens of dollars to exploit exposed, known vulnerabilities to achieve basic criminal or attention-grabbing objectives. | Mid-Tier adversaries use known TTPs to exploit known and unknown vulnerabilities at the costs of millions of dollars to achieve major criminal or national objectives. Their TTPs are generally categorized and tracked as cyber intelligence as named Advanced Persistent Threat (APT) groups. | High-Tier adversaries attack the supply chain creating their own methods and vulnerabilities (and therefore unknown). The costs are in the billions and are usually supported and funded by foreign governments seeking to gain outcomes vital to their national security. |
Leveraging an All-Threat™ Strategy
We recommend bringing an All-Threat™ Strategy to your Zero Trust Architecture to help you achieve cyber resiliency and improve business functionality. The All-Threat Strategy helps you to:
- Build for Cyber Resiliency: Limit the dependence on vulnerable technology and processes.
- Stay Ahead of Threats: Regularly adjust your security based on the nature of the threats you face.
- Develop Greater Assurance: Protect the system with out-of-band feedback to demonstrate and validate your system security.
- Evolve with Your Adversary: Leverage the latest understanding of your adversaries in your defenses.
How do I take an All-Threat™ Approach?
Not without some help. We’re here to help you understand and incorporate the necessary components to have the right set of capabilities for your mission. Contact us online at www.ardalyst.com, email us at info@ardalyst.com, or call us at (833) 682-8270 to schedule your free consultation today.