Breaking Down CUI
Every couple of weeks, I am finding myself back in the same conversation when advising clients and potential clients about the impacts of the DoD’s Cybersecurity Maturity Model Certification (CMMC). They inevitably ask:
- What is CUI, really?
- How big of a deal is it?
- What should I do about it?
- What is FCI?

What is CUI? Controlled Unclassified Information
CUI is government created or owned information that requires safeguarding or dissemination controls consistent with applicable laws, regulations and government-wide policies. CUI is not classified information. It is not corporate intellectual property unless created for or included in requirements related to a government contract.
Believe it or not, the term “Controlled Unclassified Information” has been around for about a decade. It was established under Executive Order 13556 of November 4, 2010.
To be clear, any unclassified information that requires safeguarding or dissemination control is by definition CUI. This definition comes from 32 CFR Part 2002 “Controlled Unclassified Information.”
Why is it important?
Because there are fewer controls over CUI as compared to classified information, CUI is the path of least resistance for adversaries.
Loss of aggregated CUI is the one of the most significant risks to national security, directly affecting lethality of our warfighters. There are over 1 million contracts in the NISP alone that contain DFARS Clause 252.204-7012, “Safeguarding Covered Defense Information and Cyber Incident Reporting” and over 3 million with CUI in the cleared industrial base overall.
**The information above is the prime driver behind the need for the Cybersecurity Maturity Model Certification (CMMC).**
How is CUI management changing and what should I do about it?
In May 2018, the designated senior agency official for CUI – the Under Secretary of Defense for Intelligence – designated the Defense Counterintelligence and Security Agency with DoD enterprise management of CUI. The Under Secretary of Defense for Acquisition and Sustainment is responsible for maintaining processes, policies and procedures, in accordance with DFARS, to protect DoD CUI related to contracting and agreements. The USD(A&S) is also responsible for supporting the implementation of CUI requirements into Federal Acquisition Regulations relating to defense contractors.
DFARS 252.204–7012 requires an organization or individual to have a “lawful governmental purpose” for access to CUI which, is a lower standard than the “need-to-know” required for classified access.
NIST SP 800-171 outlines standard security requirements for CUI, however, some CUI may require additional protection based on impact to national security. The security requirements for non-DoD systems storing, processing or transmitting CUI will be incorporated into all contracts and will follow DoD Instruction 8582.01, “Security of Non-DoD Information System Processing Unclassified Nonpublic DoD Information.” DoD contracts must also require contractors to monitor CUI for the potential of aggregated CUI that generates classified information.
What is FCI?
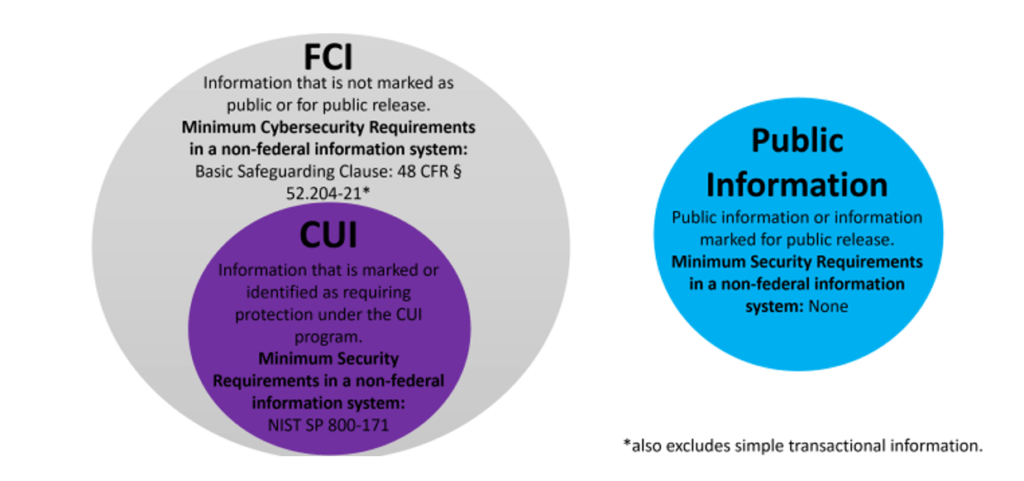
FCI in CMMC stands for “Federal Contract Information.” FCI is “information not intended for public release. It is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government. FCI does not include information provided by the Government to the public.”
FCI is a much broader dataset than CUI, but it affects audit scope and security implementations similarly to CUI. DoD Government contractors are already familiar with CUI as they are required to protect CUI in their computer systems. NIST Special Publication 800-171 describes the cybersecurity measures required to protect CUI. For the CMMC, Level 3 provides the minimum protection for CUI. In the CMMC, FCI is primarily discussed at Level 1. For organizations with CUI, the scope of the audit is limited by computer systems that could access or transmit CUI. With the CMMC applying to ALL DoD Contractors, it is critical to have an understanding of the information you have on your networks. CUI … FCI…both?
Contact Ardalyst for more information and assistance. We offer a free introductory Risk Management workshop, which is specifically designed to meet the anticipated requirements of CMMC Practice RM.2.141 and start clients on their CMMC journey today. An understanding of these basic terms is a necessary first step. Don’t take the next steps alone. Schedule a consultation to get started.
Josh O’Sullivan is the co-founder and chief technology officer for Ardalyst in Annapolis, MD.






