The Two Routes to CMMC & What You Need to Know About Each
Contractors and subcontractors working with the Department of Defense (DoD) are preparing for the Cybersecurity Maturity Model Certification (CMMC) and starting to research ways to get their businesses compliant. If you’re looking to get some external help, there are two main routes that you can take: the consulting route or the managed service route. In this blog post, we’ll dive into the differences between these two options and help you decide the best one for your business.
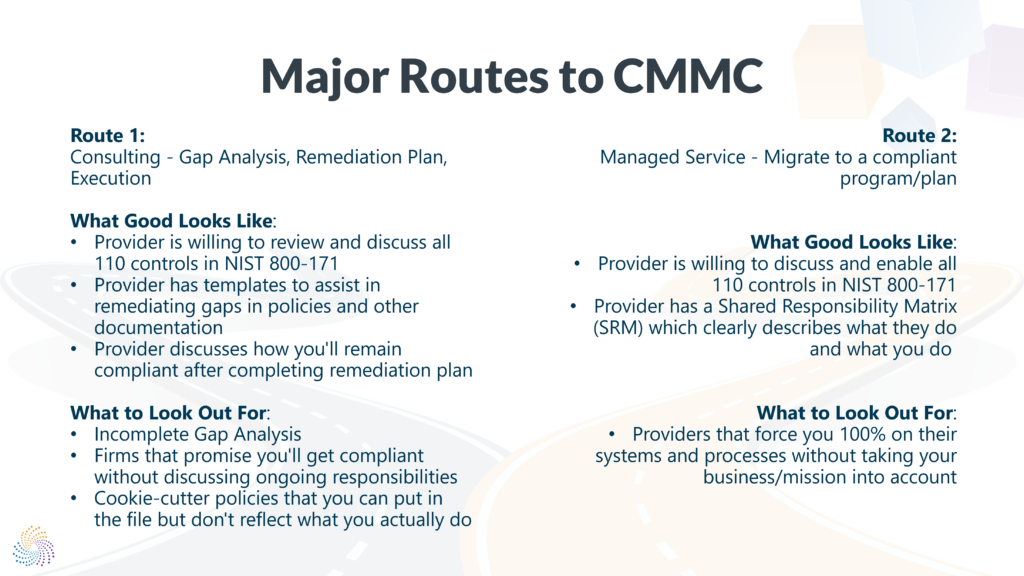
Route 1 – Consulting
The consulting route is the most common approach offered by most Registered Provider Organizations (RPOs) and Certified 3rd Party Assessment Organizations (C3PAOs). RPOs are firms that have been authorized by the CMMC Accreditation Body (CMMC-AB) to provide pre-assessment guidance and readiness services to DoD contractors. C3PAOs are firms that have been authorized to perform assessments, and many are providing pre-assessment services on the condition that they will not be able to provide the full certification assessment in the future.
The consulting route typically involves the firm providing a gap analysis, a remediation plan for the gaps they identified, and – in some cases – services to close those gaps. The consulting route can be a good option if you have a large or complex IT environment or want to have more control over your cybersecurity processes.
What Good Looks Like
A good consulting engagement is going to be willing to review and discuss all 110 controls in NIST SP 800-171 Rev 2 with you to make sure that you understand what is expected of you and how you can achieve full compliance. A good provider will most likely provide templates to assist with developing your policies and other documentation to set you on the right path to remediating your gaps. Last, a good provider will be able and willing to discuss with you how you’ll be able to remain compliant after completing the remediation plan. This ability is crucial for your ongoing success. Compliance includes activities that must be done daily, weekly, monthly, quarterly, and annually which you must be able to execute. Your CMMC certification is only good for 3 years so not only do you need to keep up these activities to stay compliant, but you’ll also need to maintain your compliance to be able to recertify.
What Bad Looks Like:
A bad consulting engagement is going to promise that you’ll pass certification and is going to be more interested in selling you their services than helping you achieve compliance. They may not explain the controls in detail, or they may use generic templates that do not fit your specific needs. They may also overpromise and underdeliver on their remediation plan, leaving you with unresolved gaps and vulnerabilities. Worse, they may not provide any guidance on how to maintain compliance after the project is done, leaving you exposed to future audits and penalties. Look out for contracts that don’t address all the control families and don’t address all 110 controls, and don’t discuss with you how you’ll operate and maintain the controls after they are gone.
How to Choose a Good Consulting RPO
To avoid falling into the trap of a bad consulting RPO, you need to do your homework and ask the right questions. Here are some tips on how to choose a good consulting RPO:
- Check their credentials. Make sure they are registered with the CMMC Accreditation Body (CMMC-AB) and have qualified staff who are trained and certified in CMMC.
- Ask for references. Ask for testimonials or case studies from previous clients who have achieved CMMC compliance with their help. Contact those clients and ask about their experience, satisfaction, and results.
- Compare prices. Compare the fees and scope of services offered by different RPOs. Don’t go for the cheapest option, but also don’t overpay for unnecessary services. Look for a fair and transparent pricing model that aligns with your budget and goals.
- Request a proposal. Ask for a detailed proposal that outlines the steps, timeline, deliverables, and expectations of the project. Review the proposal carefully and make sure it covers all aspects of CMMC compliance, from gap analysis to remediation to maintenance.
- Make sure it’s comprehensive. Ask about all the control families and make sure that the analysis they provide will identify the things you’ll need to do after the consulting engagement is over and they are gone.
- Beware low initial prices. If your proposal doesn’t include remediation and doesn’t talk about how you’ll perform ongoing duties, ask about the costs for those activities.
Route 2 – Managed Service
The managed service route involves either migrating to a compliant program or plan or hiring a provider to help you maintain your compliant systems. This can be a very cost-effective approach for small and mid-sized businesses that need to outsource IT support, have IT support but not cybersecurity expertise, or need the expertise, personnel, guidance, and ongoing support that a managed service provider can provide. The MSP will take care of the technical aspects of CMMC compliance, such as configuring, monitoring, patching, and updating your systems, as well as providing evidence and documentation for audits. The managed service route can be a good option if you have a simple or cloud-based IT environment, have an outdated IT infrastructure that will be expensive to make compliant, do not have the in-house expertise or the size of the team that can perform your security functions, or want to have more peace of mind about your cybersecurity posture.
What Good Looks Like
A good MSP – please note that all MSPs aren’t RPOs, you’ll want to make sure you choose one who is an RPO and certified to provide CMMC services – will be able and willing to discuss and enable all 110 NIST SP 800-171 Rev 2 controls to get you to full compliance. The provider you choose should also be able to provide guidance, training, and documentation to your business and its employees to guarantee you can properly run your program. A good provider will also have a Shared Responsibility Matrix (SRM) which clearly describes what activities they are responsible for, and what activities you are responsible for. Ensure that your provider can respond to incidents, audits, and changes in the CMMC framework. Cybersecurity is ever-evolving, and neither your business nor your program should ever be stagnate in the fight against cyber threats.
What Bad Looks Like
Avoid providers that force you 100% onto their systems and processes without taking your business/mission into account. There is a way to achieve compliance while putting your business and goals first that can make your cybersecurity program a business enabler instead of a hindrance. There are also low-cost approaches to having a small separate compliant environment that you still own and control. Be careful to understand where your data is going to reside and what you will need to do if you change providers in the future; a bad contract will lock you in beyond just the term of the contract by making it difficult to switch. Last, some providers might have the IT experience but not security experience. You’ll want a provider that can do both.
How to Choose a Good Managed Service RPO
To avoid a bad managed service provider, take some of the following steps to help you make the best decision for your business:
- Research and compare different providers based on the comprehensiveness of their offering, qualifications, and reputation. Does the provider understand both the cyber and IT aspects of your program?
- Request a quote. The quote should be able to provide clear, definitive pricing without any surprises.
- Ensure that the offering is aligned with your business’s needs. This means that the cheapest option isn’t necessarily the best option. Look for cost-effectiveness together with what you need from your provider. Your provider should have options for different architectures depending on how your business works.
- Avoid one-size-fits-all. It’s possible to provide you with flexibility without sacrificing cost. If you need everything handled, look for a firm that can do that, and if you want to save money by having your team handle certain elements of the program, look for a provider that can work with you.
- Do not sign a contract that does not specify the roles, responsibilities, expectations, and deliverables of both parties. Again, this is something that is typically solved by a Shared Responsibility Matrix (SRM), ensure your provider has one.
How Ardalyst Can Help
Ardalyst’s Tesseract is a Managed Cybersecurity Program (or Route 2) that was built to help small and midsized businesses implement a comprehensive program to comply with regulatory requirements and improve your cybersecurity posture without the expensive price tag of most cybersecurity solutions on the market.
If you haven’t gotten started with your NIST 800-171/CMMC compliance, take advantage of our free resources to get you started.
- Get your free risk assessment. Meet the requirements for RA.L2-3.11.1 and lay out the foundation for your comprehensive cybersecurity program.
- Start your free Tesseract trial. Not only receive your free risk assessment but gain a free:
- An overview of the Tesseract Managed Cybersecurity Program and your path to getting & staying compliant
- A technical design of your Tesseract program enclave
- A migration plan to get you into your compliant environment.
- Exclusive deals on additional tools like Microsoft 365.






